Prerequisites
Before you begin, ensure you have the following:- Keycloak installed
- Administrative access to the Keycloak server
- Basic understanding of IAM concepts
Recommended Keycloak setup
To configure a minimal required Keycloak setup, this guide covers the following steps:Add clients
Keycloak documentation
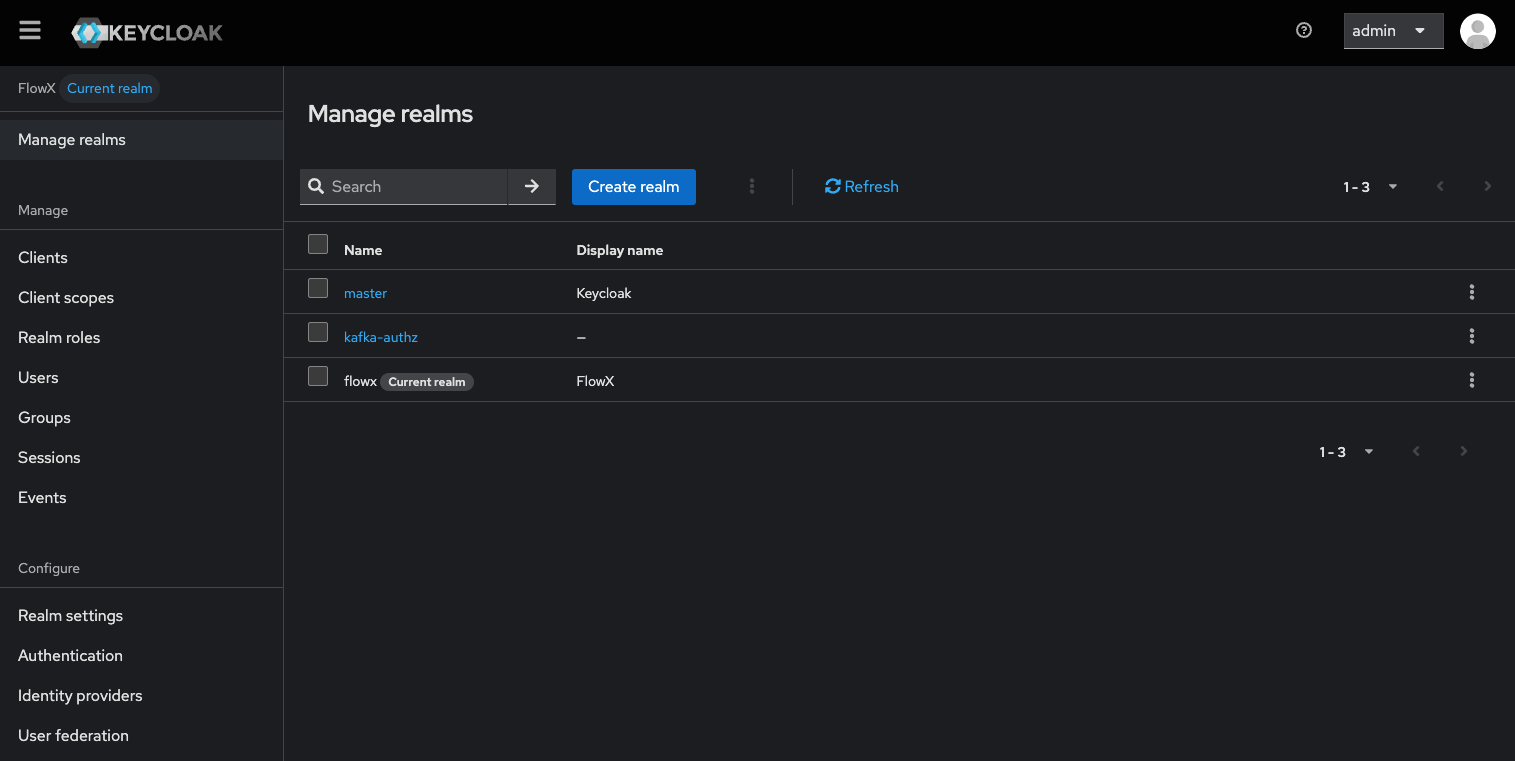
Creating a new realm
A realm is a space where you manage objects, including users, applications, roles, and groups. Creating a new realm is the first step in setting up Keycloak. Follow the steps below to create a new realm in Keycloak:Log in to the Keycloak Admin Console
Create Realm
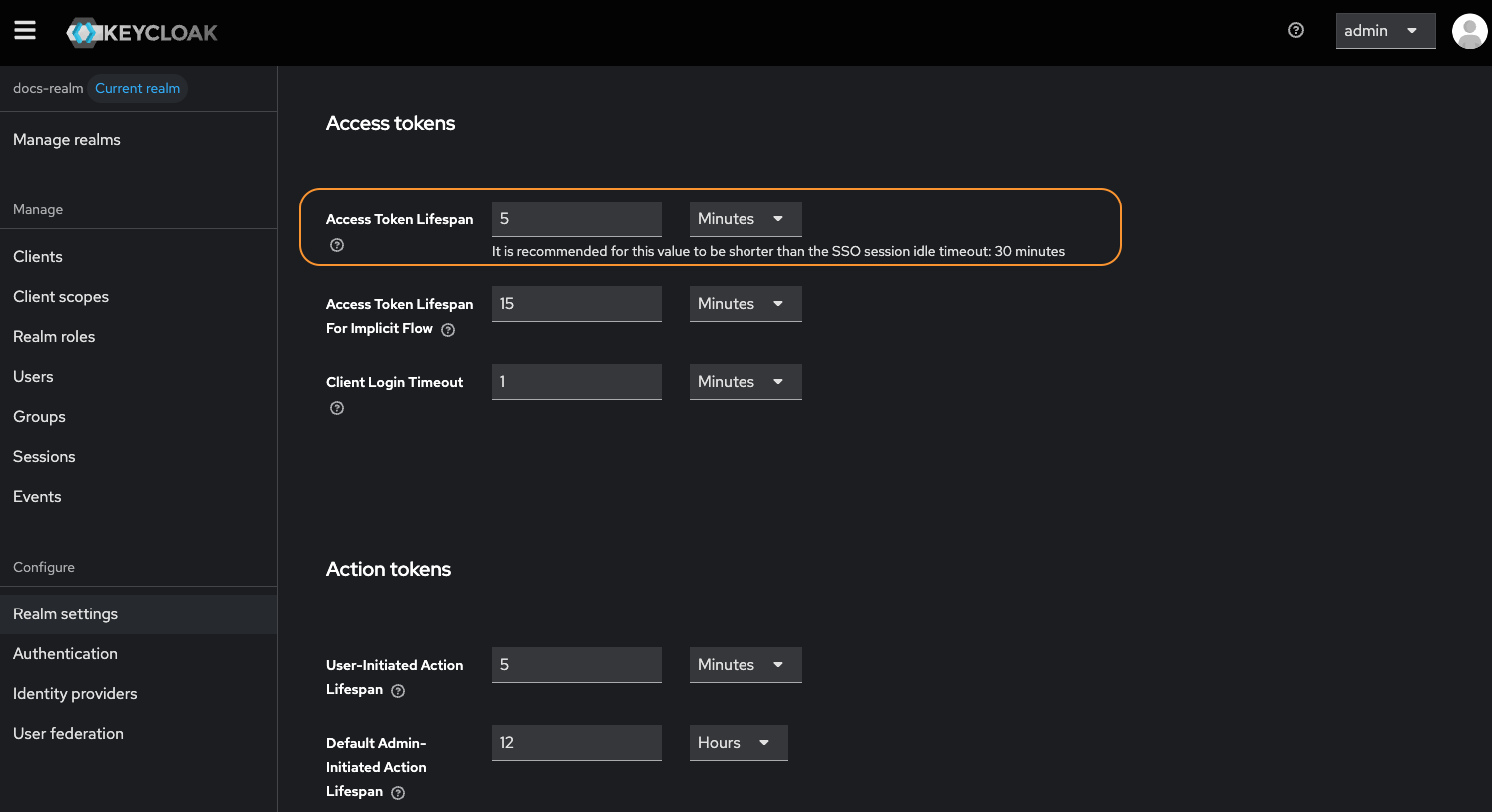
- Ensure that the realm name is unique within your Keycloak instance.
- Double-check session idle and token lifespan settings to align with your security requirements.
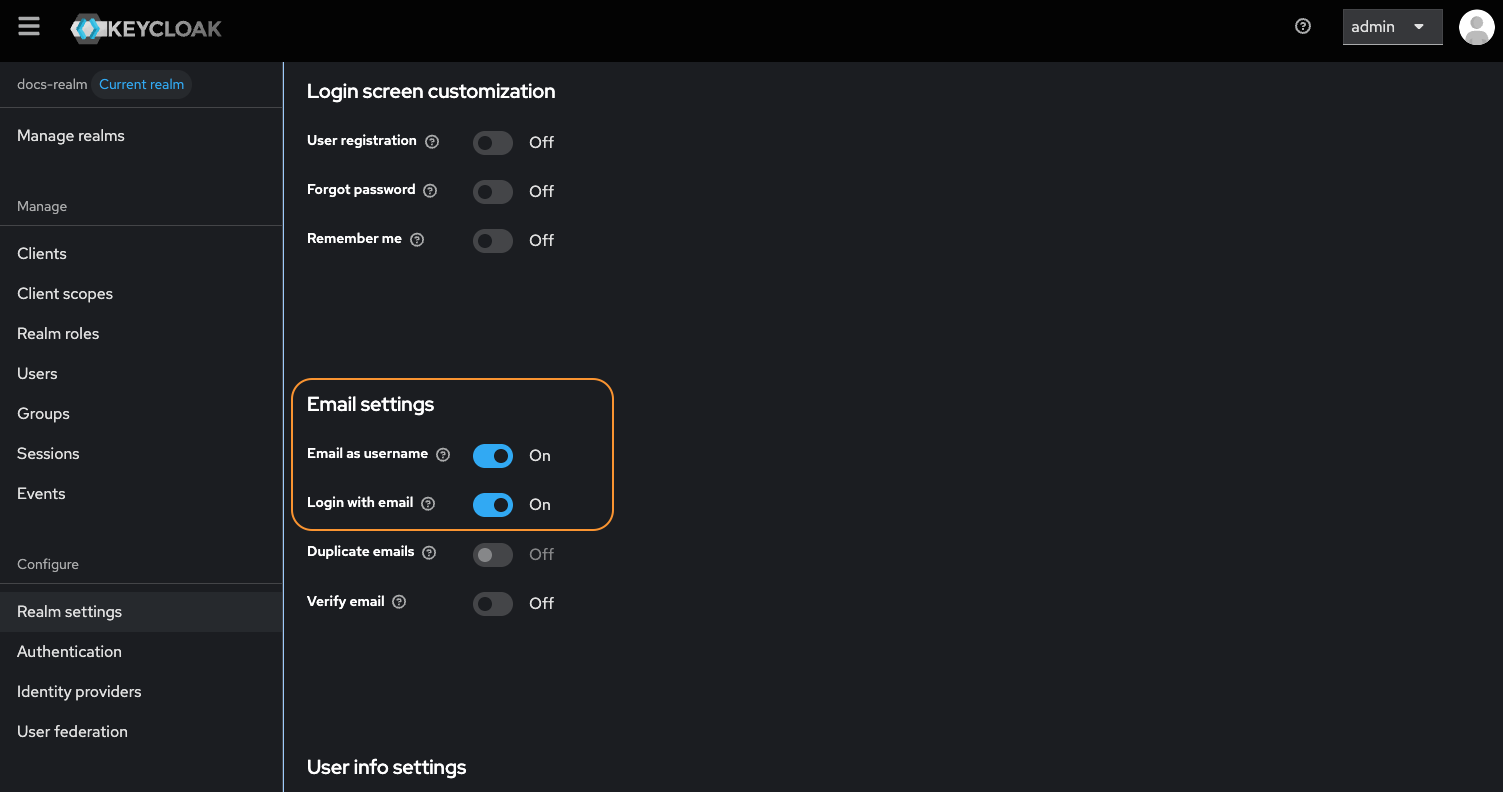
- For Keycloak 26+: Failing to configure email settings in the Login tab will result in bad request errors when creating users through FlowX Designer. Always enable “Email as username” and “Login with email” options.
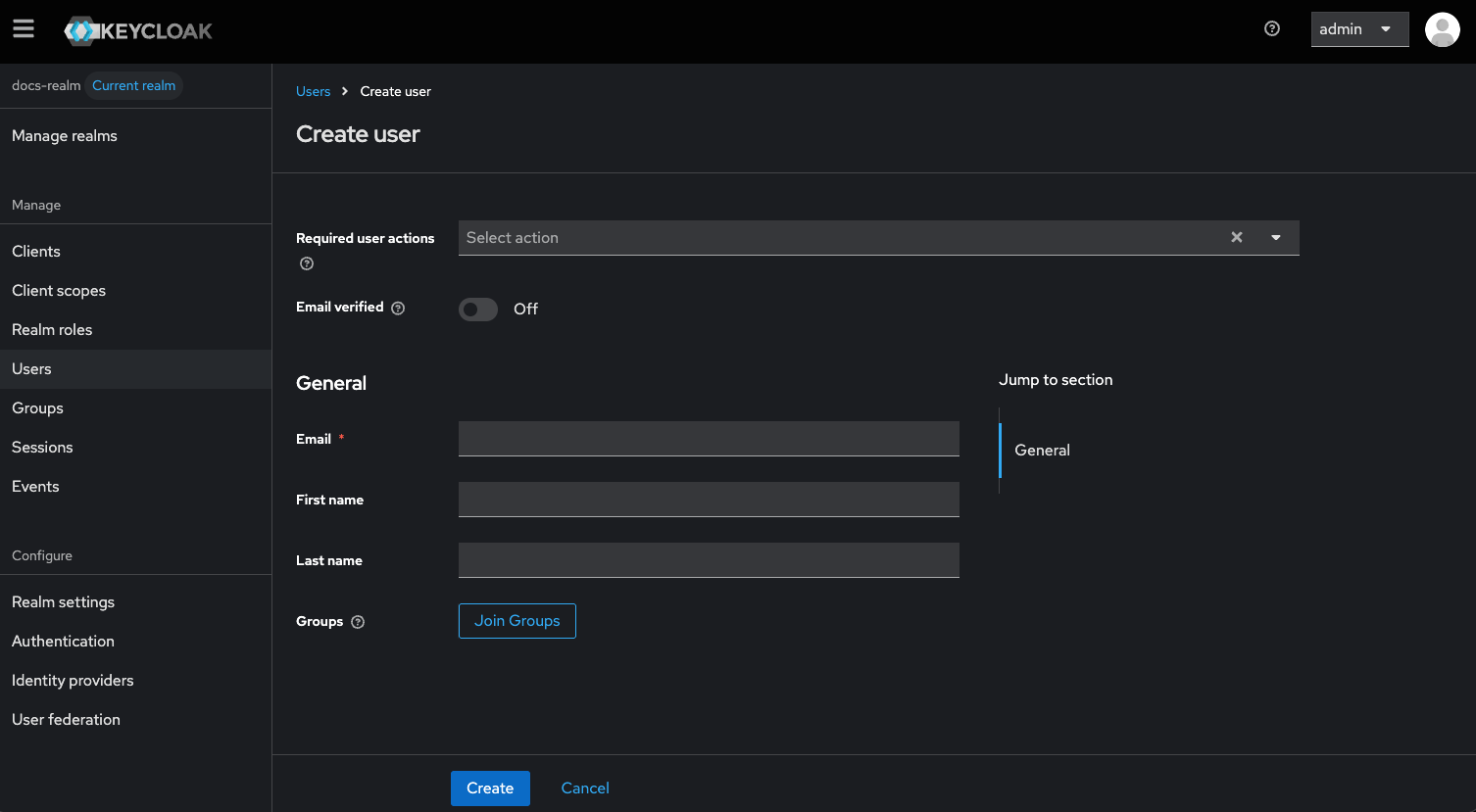
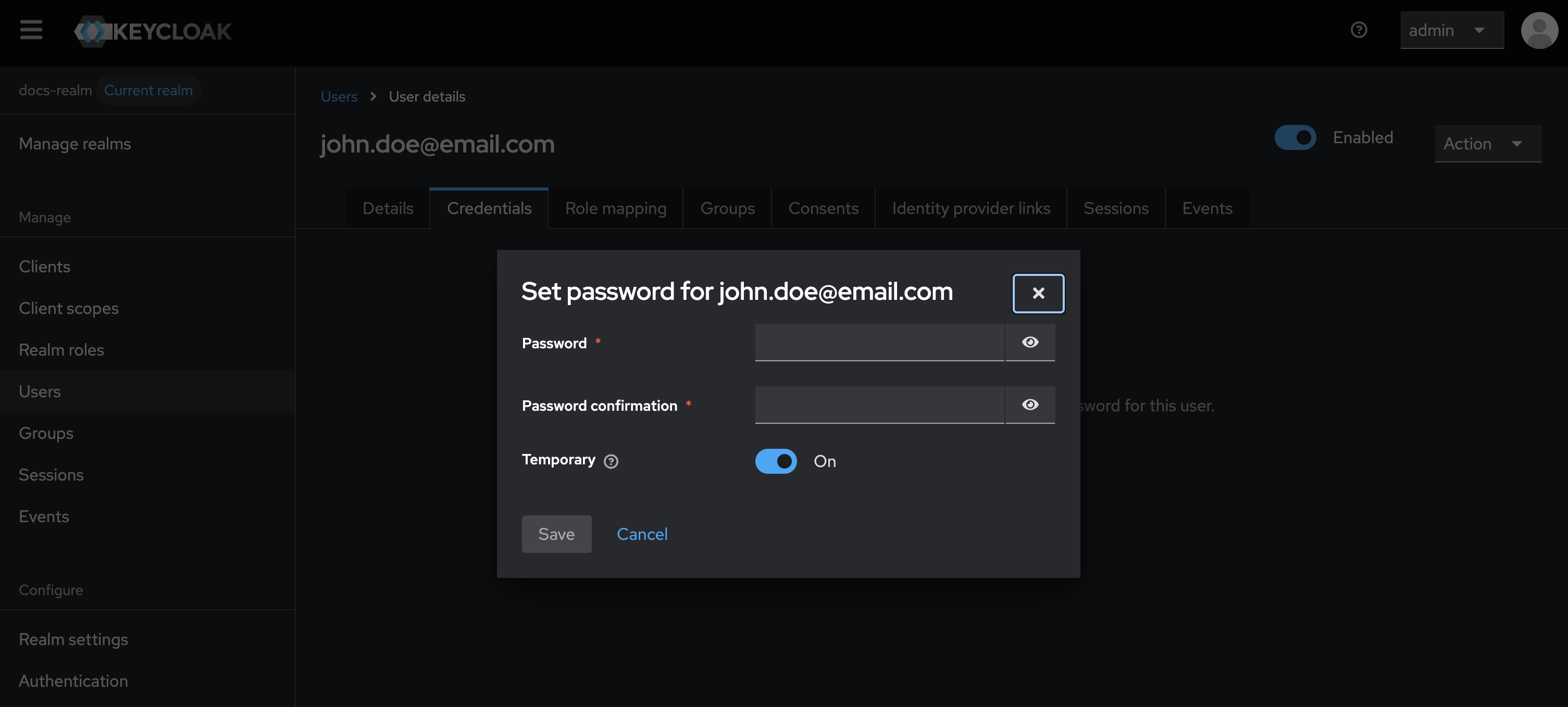
Creating new users
Creating new users is a fundamental part of managing access within Keycloak. Follow these steps to create a new user in a realm and generate a temporary password:- Ensure that the email address is valid and correctly formatted.
- Set the temporary password policy according to your organization’s security requirements.
Password policy
| Rule | Requirement |
|---|---|
| Minimum length | 8 characters |
| Maximum length | 64 characters |
| Uppercase | At least one uppercase letter |
| Lowercase | At least one lowercase letter |
| Number | At least one digit |
| Special character | At least one of !@#$%^&*()_+- |
| Additional | Cannot match the user’s email address |
Adding clients
A client represents an application instance that is associated with a specific realm.Adding an OAuth 2.0 client
We will add a client namedflowx-platform-authenticate, which is used for login, logout, and refresh token operations by web and mobile applications.
Configure General Settings
- Set a client ID to
{your-client-name}-authenticate. - Set the Client type to
OpenID Connect.
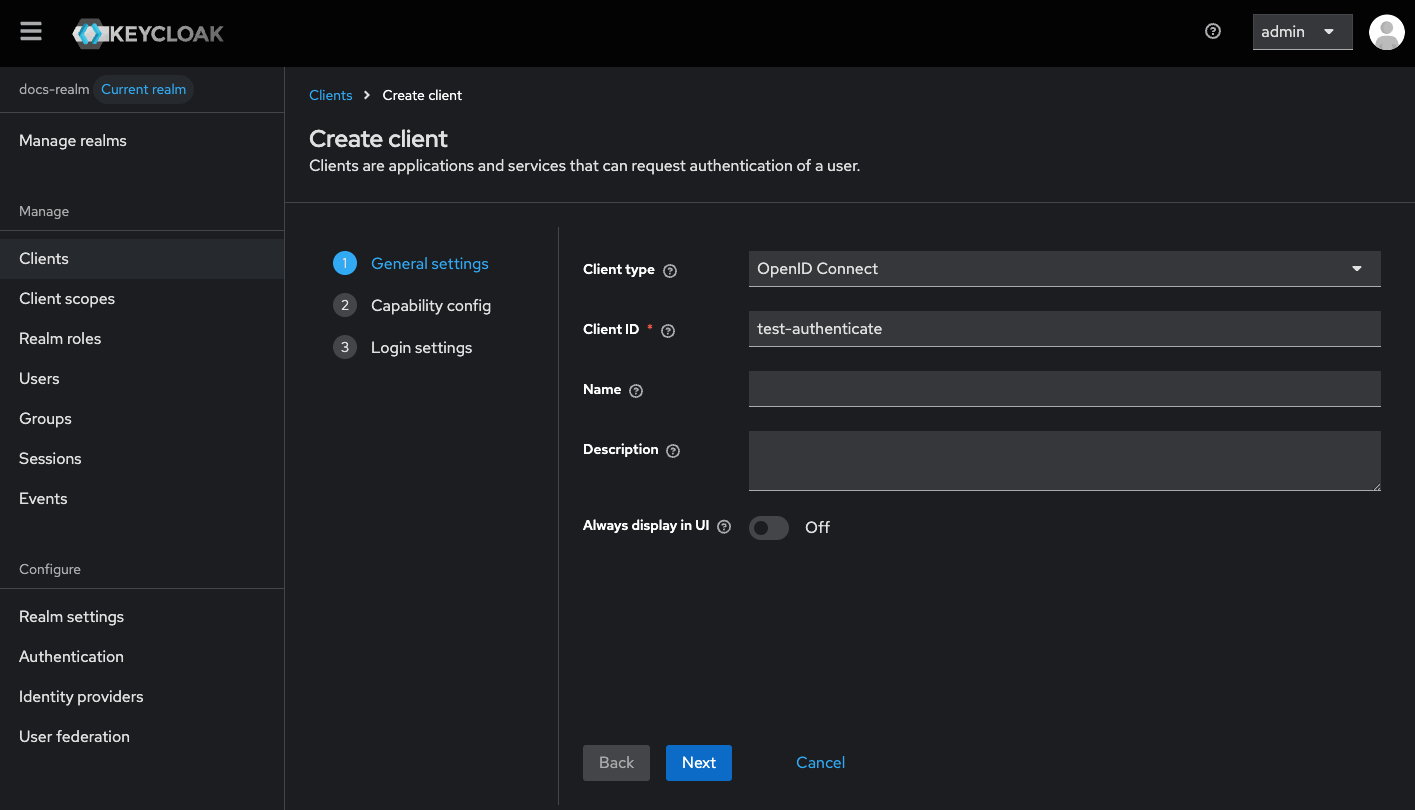
Configure Capability Config
- Enable Direct Access Grants.
- Enable Implicit Flow Enabled.
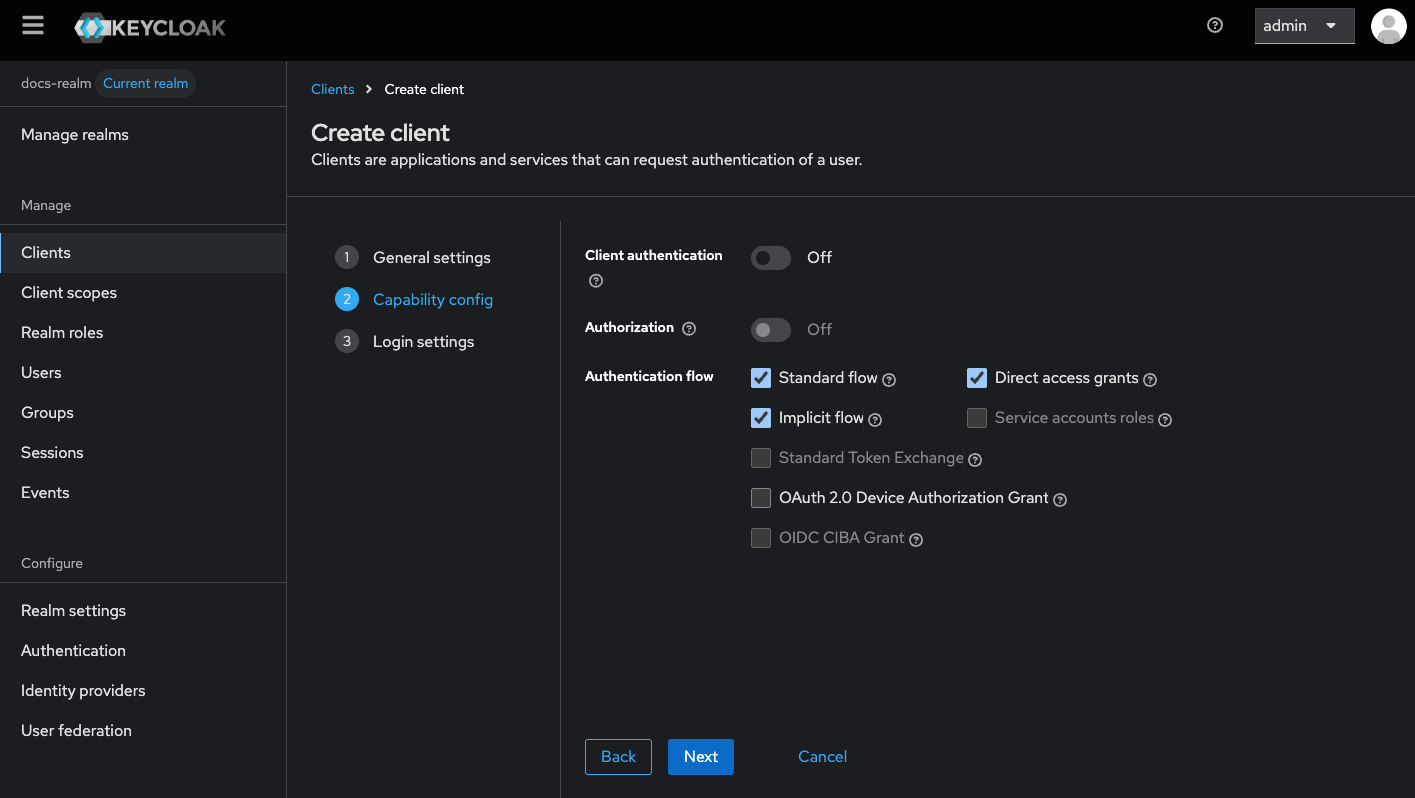
Set Valid Redirect URIs
- Set Valid redirect URIs, specifying a valid URI pattern that a browser can redirect to after a successful login or logout, simple wildcards are allowed.
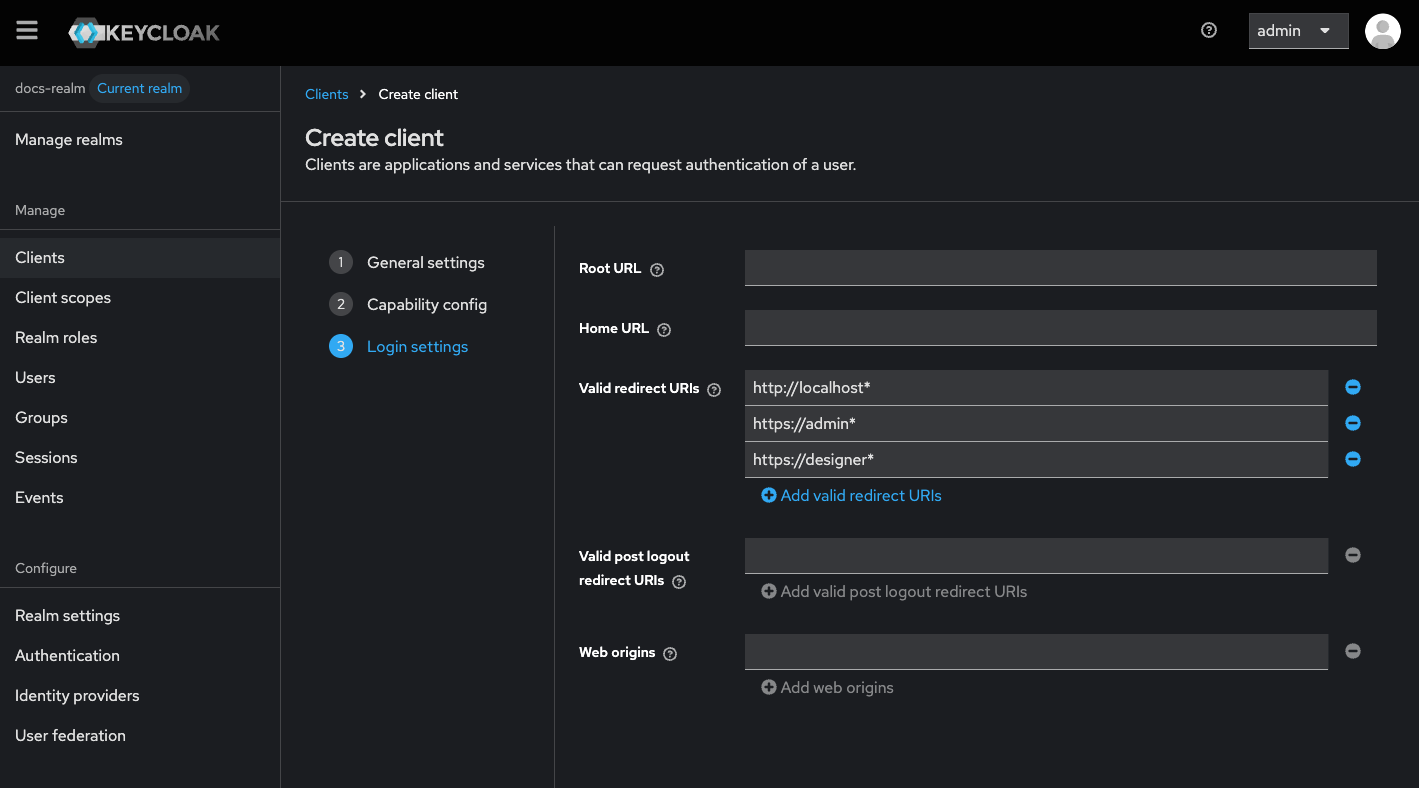
Configure Additional Settings
- Front Channel Logout: Toggle OFF.
- Backchannel Logout Session Required: Toggle OFF.
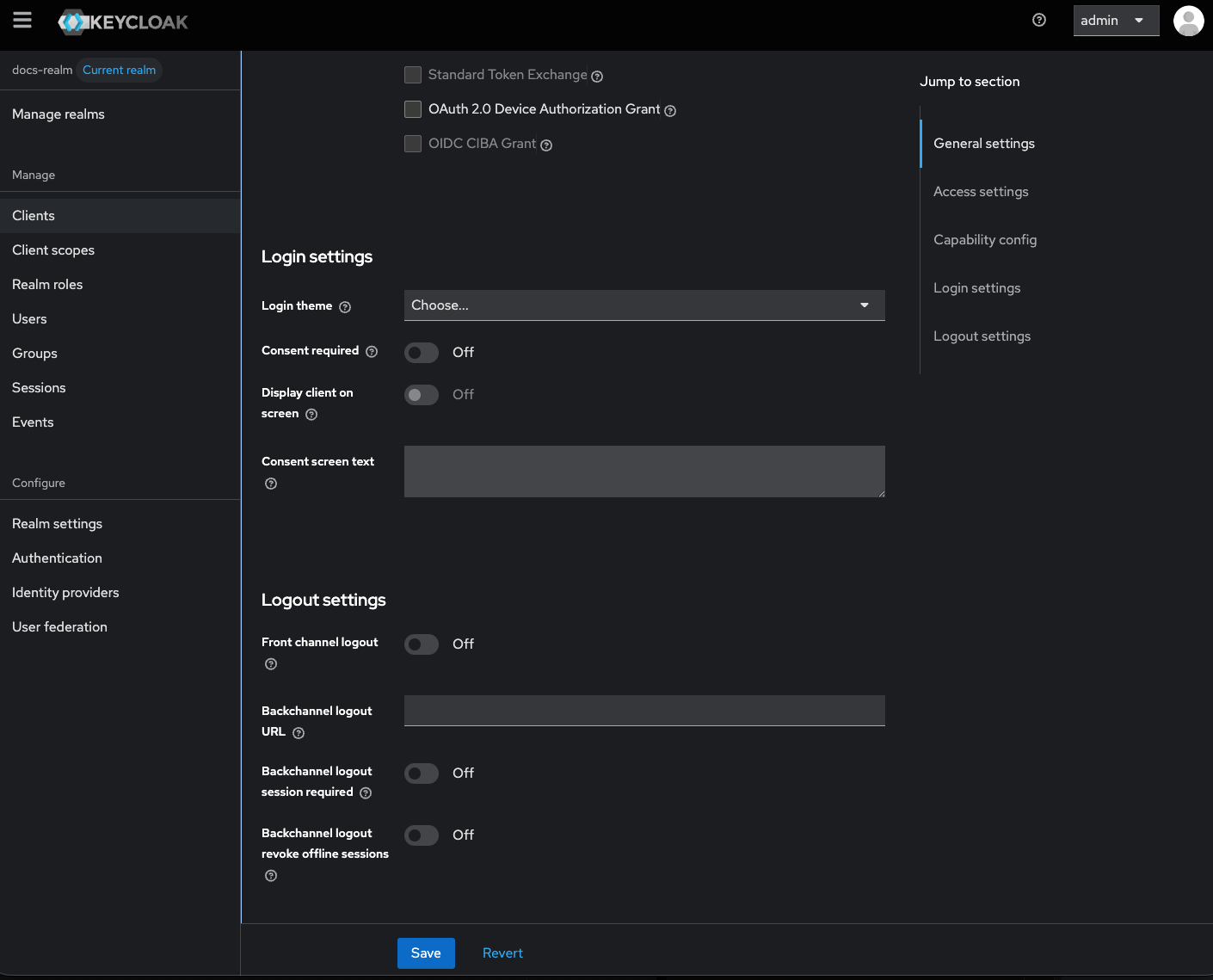
Add Mappers
{your-client-name}-authenticate client.Adding an Authorizing client
Create and configure the{your-client-name}-platform-authorize client to authorize REST requests to microservices and Kafka.
Create the Client
{your-client-name}-platform-authorize).Set Client type to OpenID Connect.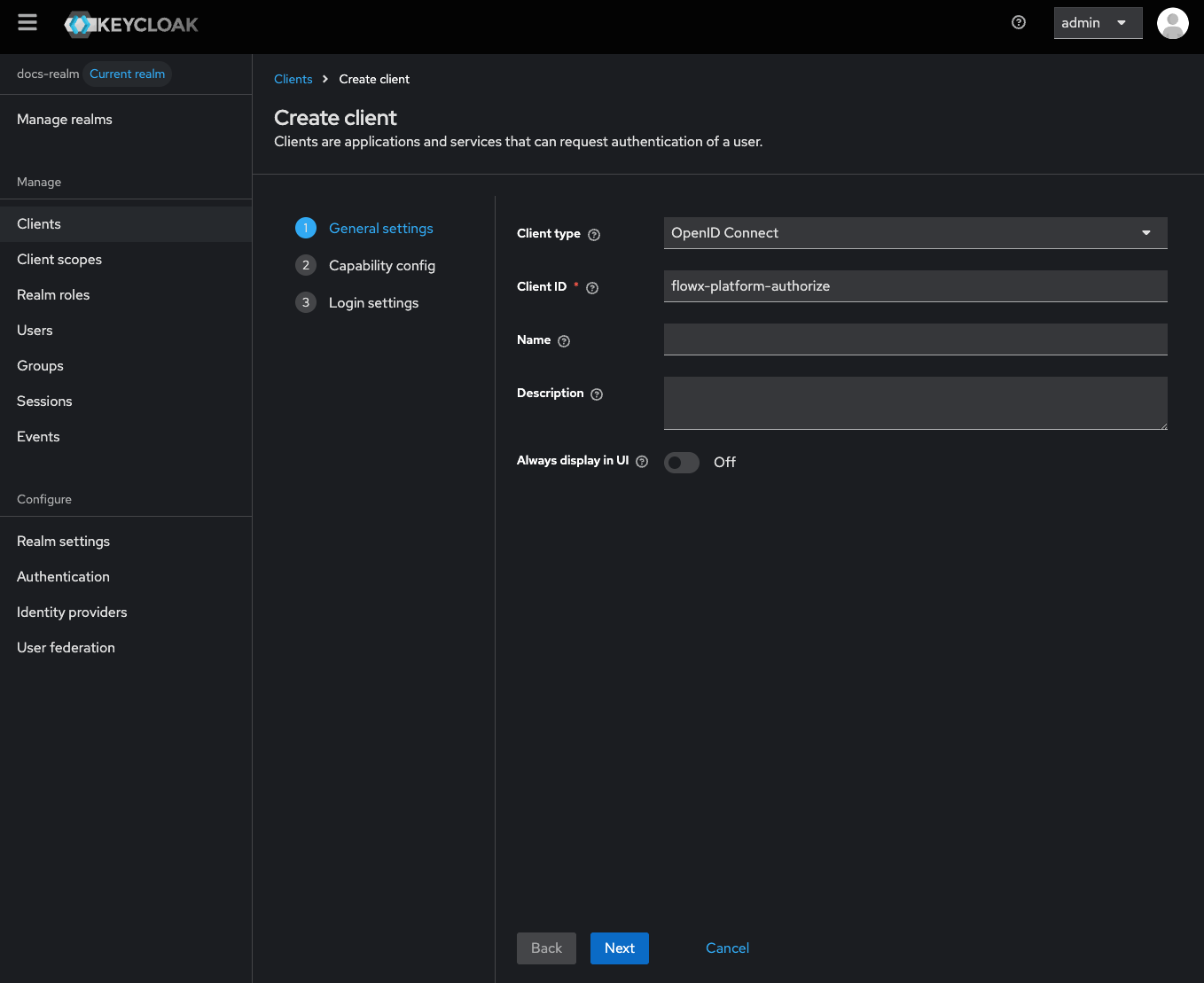
Configure Capability Config
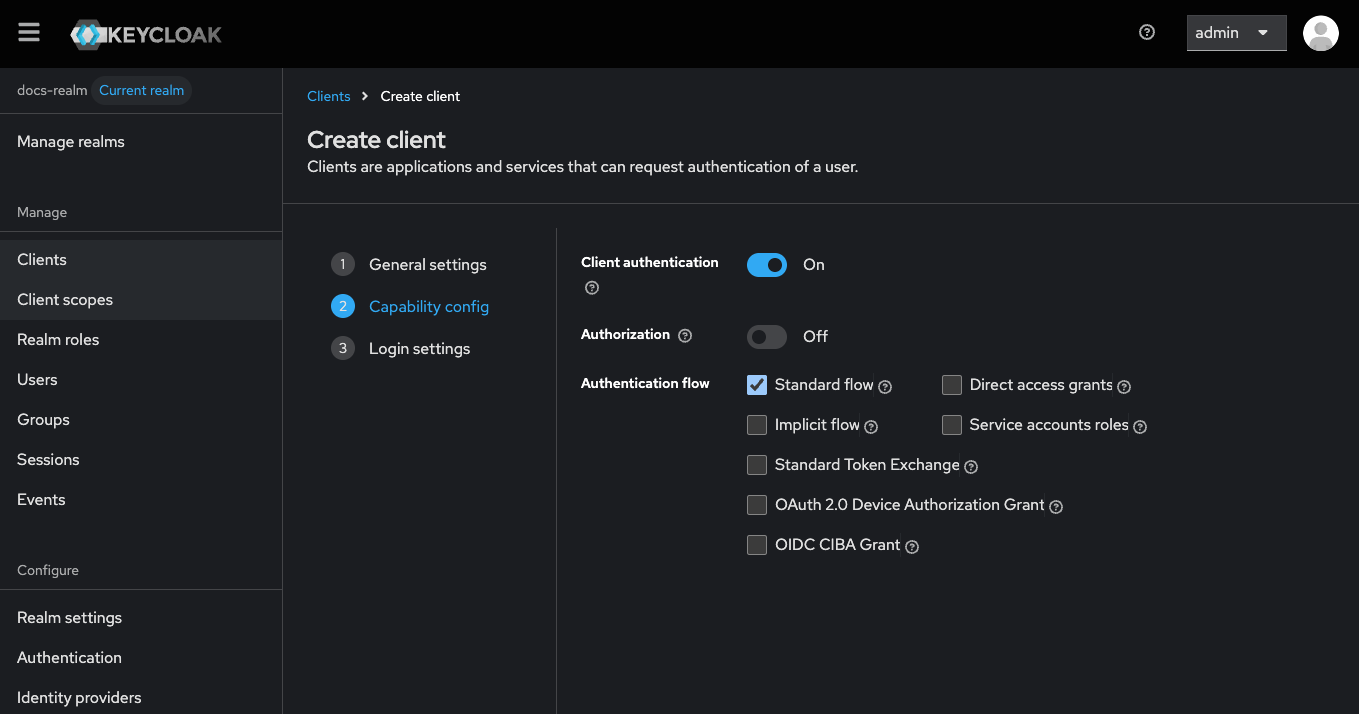
Set Valid Redirect URIs
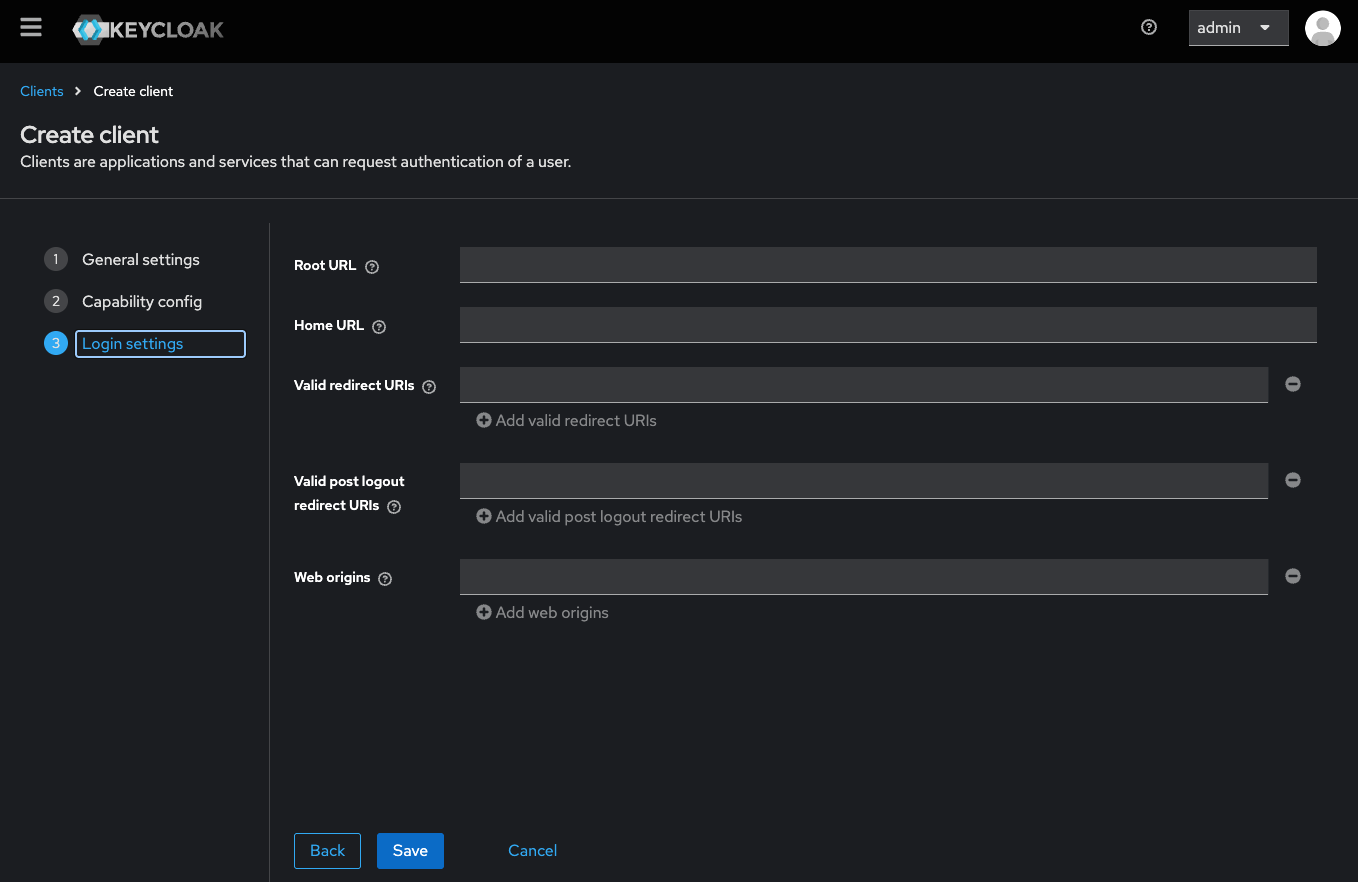
{your-client-name}-platform-authorize client will be created and can be used to authorize REST requests to microservices and Kafka within your application.
Example configuration for microservices
SECURITY_TYPE has changed from oauth2 to jwt-public-key. Services now validate JWT tokens locally using public keys from a JWKS endpoint instead of calling the token introspection endpoint. Each service uses its own service account with the client_credentials grant type.| Configuration Key | Value/Example | Description |
|---|---|---|
security.type | jwt-public-key | Validates JWT tokens locally using JWKS public keys. |
security.oauth2-client | enabled | Enables the OAuth2 client for service-to-service calls. |
security.oauth2.base-server-url | https://keycloak.example.com | Base URL of the Keycloak server. |
security.oauth2.sa-realm | 00000002-0002-4002-8002-000000000002 | The dedicated service accounts realm ID. |
spring.security.oauth2.client.registration.mainIdentity.client-id | flowx-{service-name}-sa | Service account client ID (e.g., flowx-process-engine-sa). |
spring.security.oauth2.client.registration.mainIdentity.client-secret | CLIENT_SECRET | Service account client secret. |
spring.security.oauth2.client.registration.mainIdentity.authorization-grant-type | client_credentials | OAuth2 grant type for service-to-service authentication. |
spring.security.oauth2.client.provider.mainAuthProvider.token-uri | ${security.oauth2.base-server-url}/realms/${security.oauth2.sa-realm}/protocol/openid-connect/token | Token endpoint in the service accounts realm. |
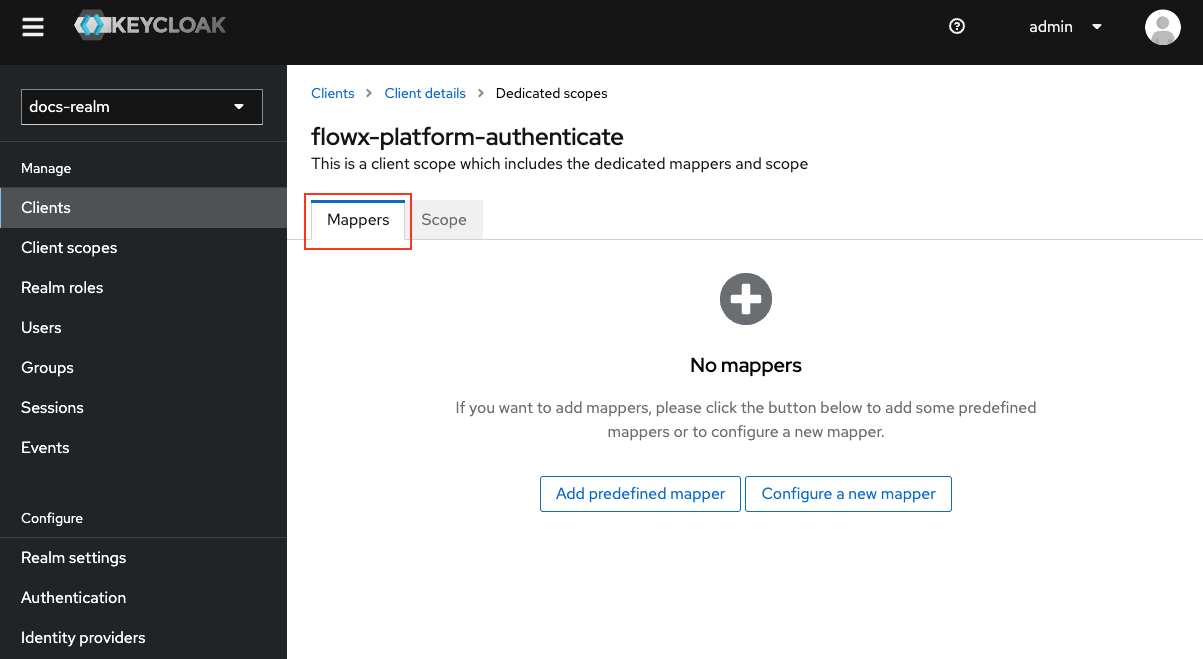
Adding protocol mappers
Protocol mappers in Keycloak allow you to transform tokens and documents, enabling actions such as mapping user data into protocol claims and modifying requests between clients and the authentication server. This provides greater customization and control over the information contained in tokens and exchanged during authentication processes.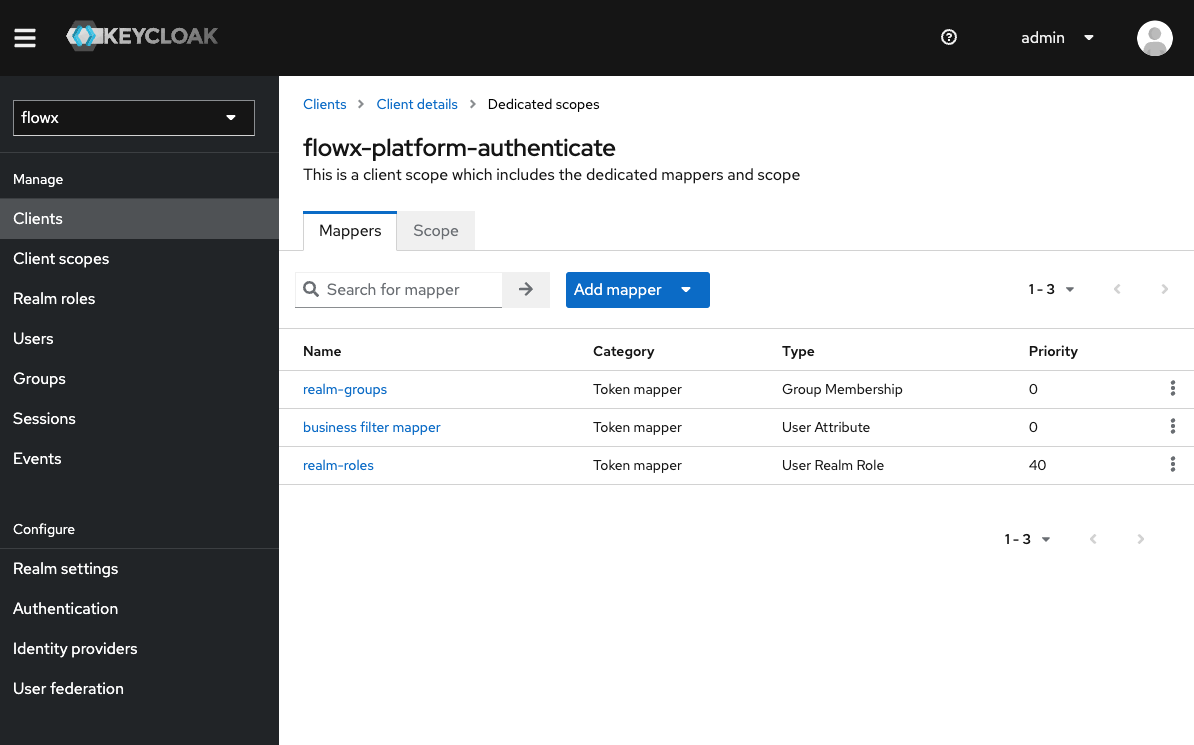
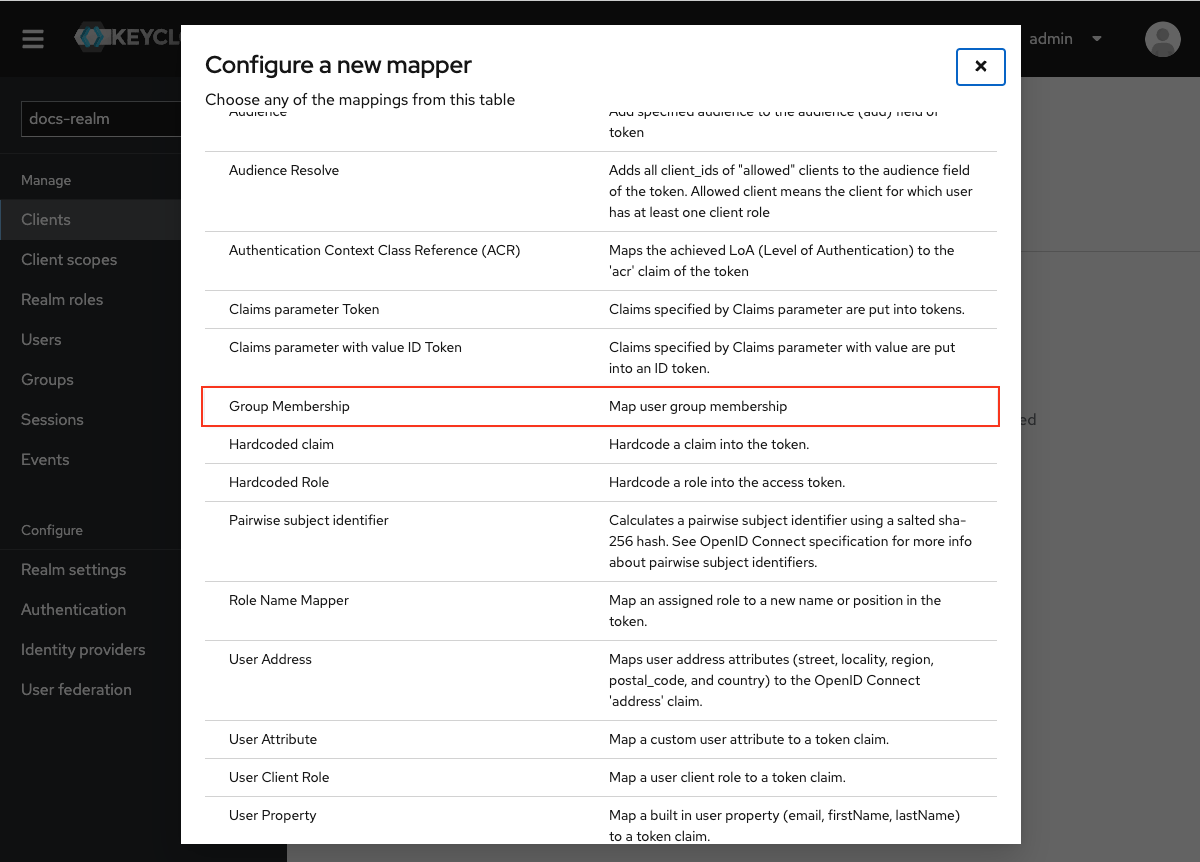
- Group Membership mapper (
realm-groups)- Maps user groups to the authorization token.
- User Attribute mapper (
business filter mapper)- Maps custom attributes, for example, mapping the businessFilters list, to the token claim.
- User Realm role (
realm-roles)- Maps a user’s realm role to a token claim.
/userinfo endpoint, but modern Keycloak versions support adding them to token introspection, which is the recommended approach for better security and performance.Group Membership mapper
Steps to add a Group Membership mapper:Select Client Scopes
{your-client-name}-authenticate-dedicated to open its settings.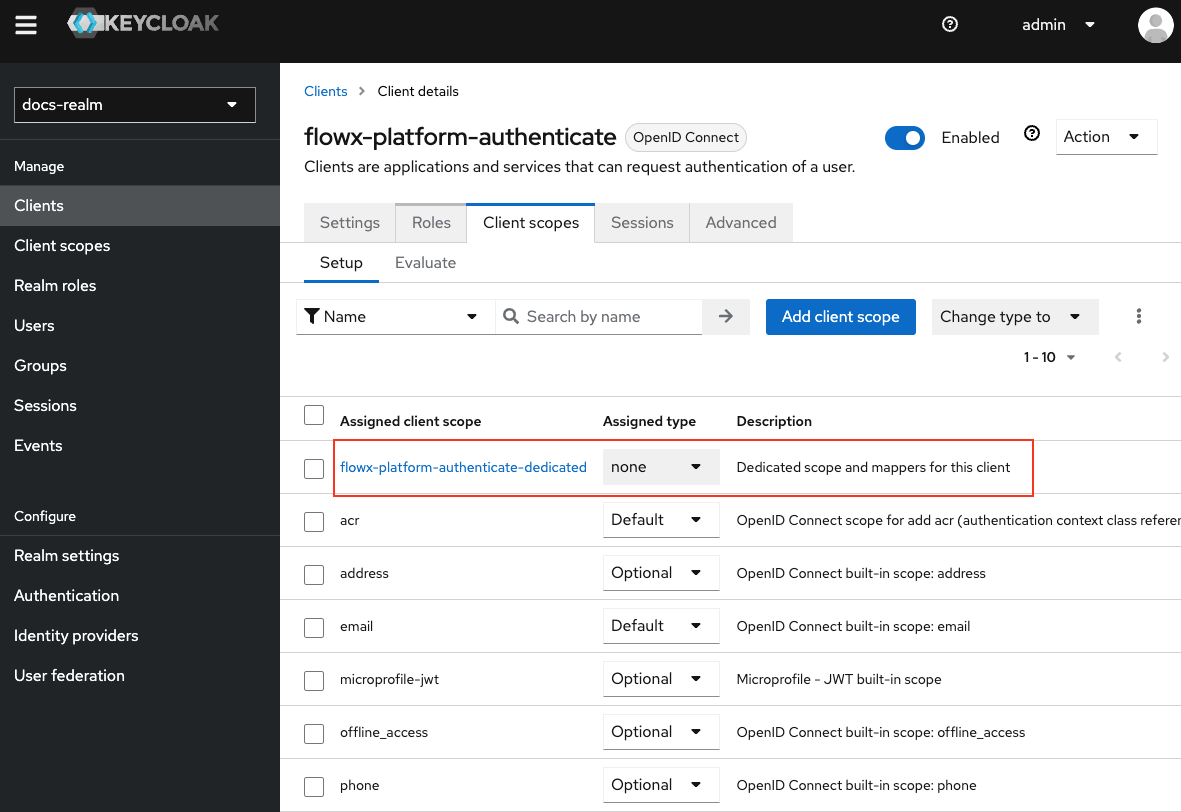
Provide Mapper Details
realm-groups.Token Claim Name: Set the token claim name, typically as groups, for including group information in the token.Add to ID Token: Toggle OFF.Add to token introspection: Toggle ON.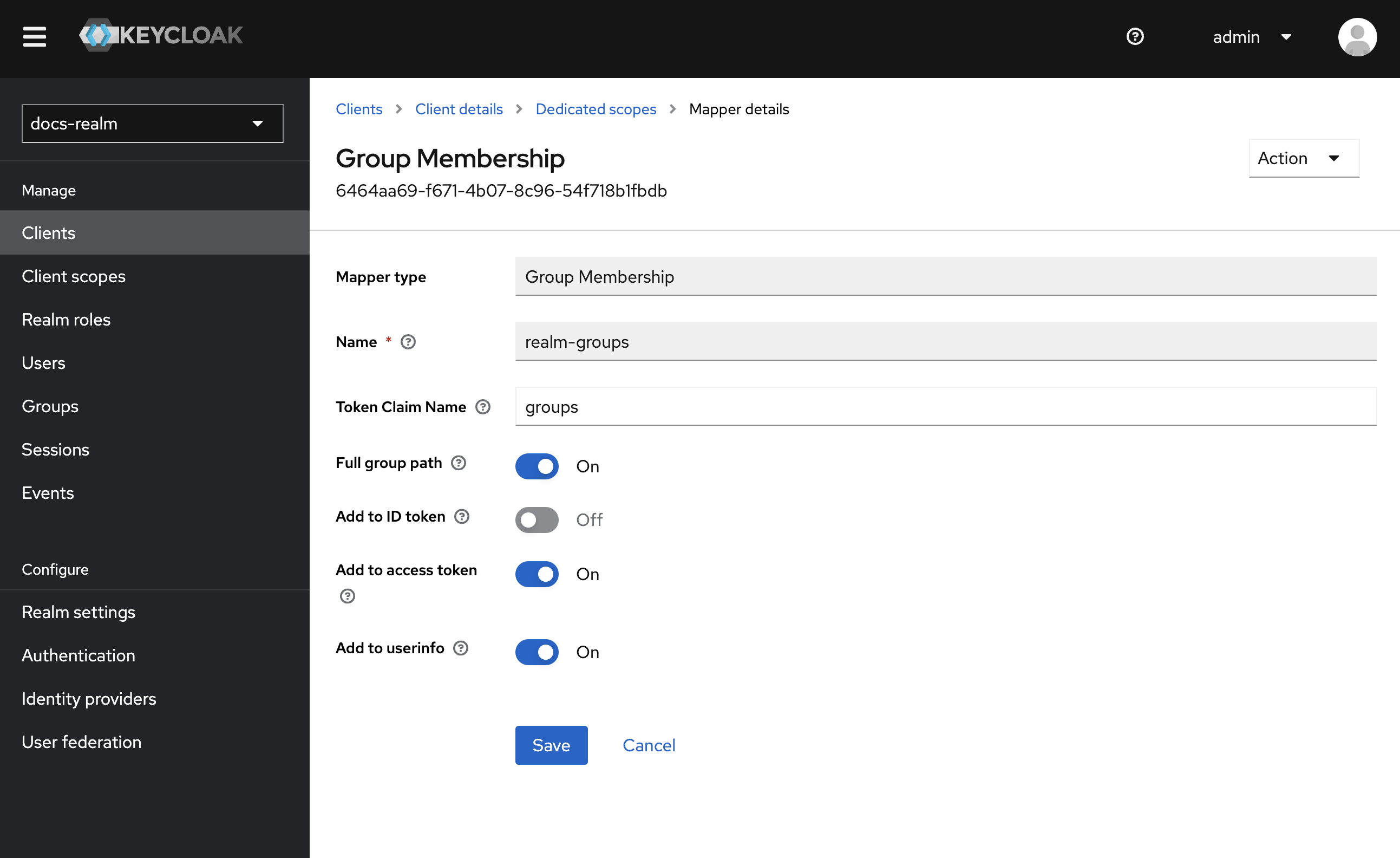
User Attribute mapper
To include custom attributes such as business filters in the token claim, follow these steps to add a user attribute mapper:Navigate to Client Scopes
{your-client-name}-authenticate-dedicated to open its settings.Ensure the Mappers tab is selected.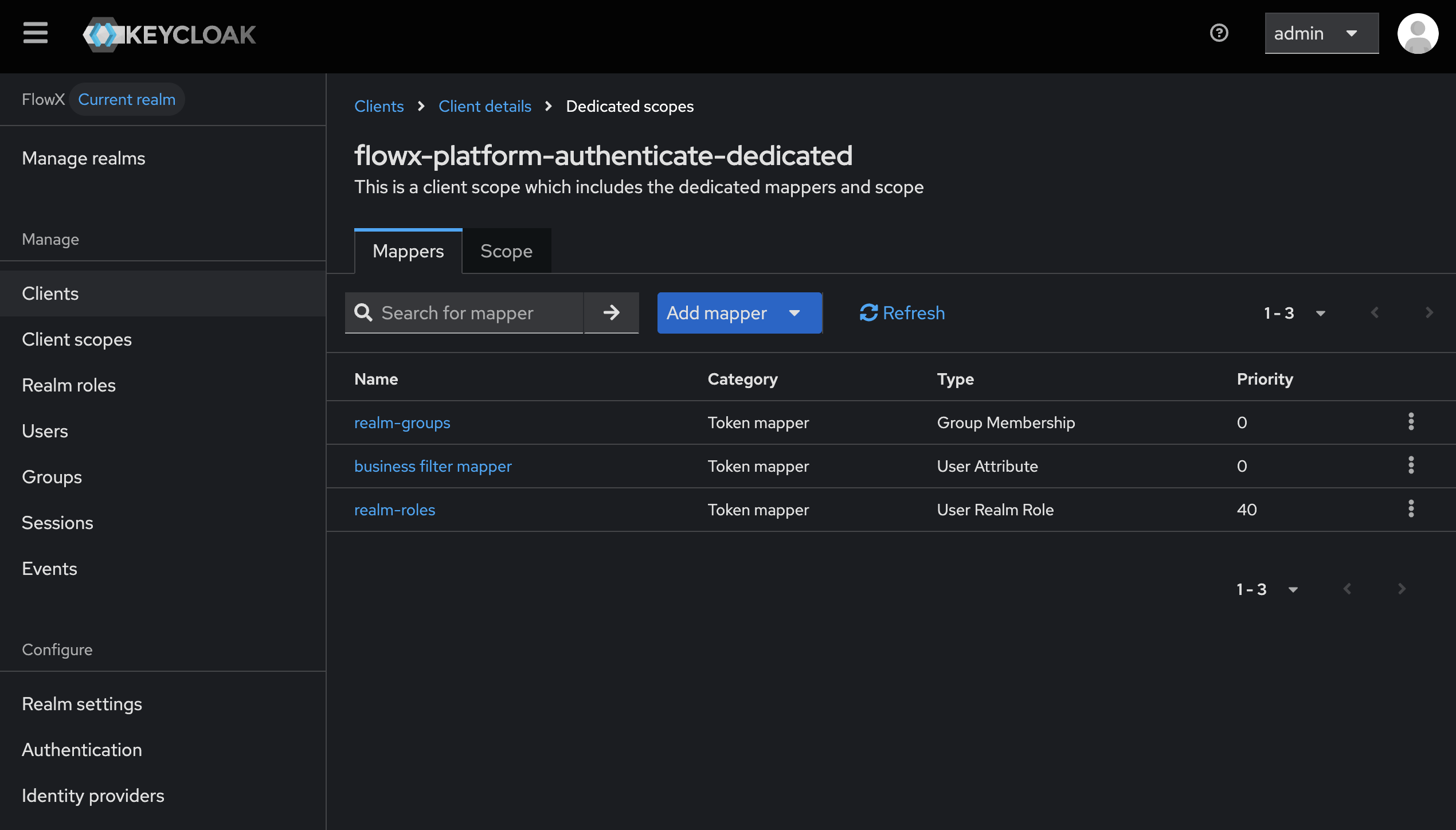
Provide Mapper Details
- Mapper Type: Select User Attribute.
- Name: Enter a descriptive name for the mapper, such as “Business Filters Mapper”.
- User Attribute: Enter
businessFilter. - Token Claim Name: Enter
attributes.businessFilters. - Add to access token: Toggle ON.
- Add to token introspection: Toggle ON (recommended).
- Multivalued: Toggle ON.
- Aggregate attribute values: Toggle ON.
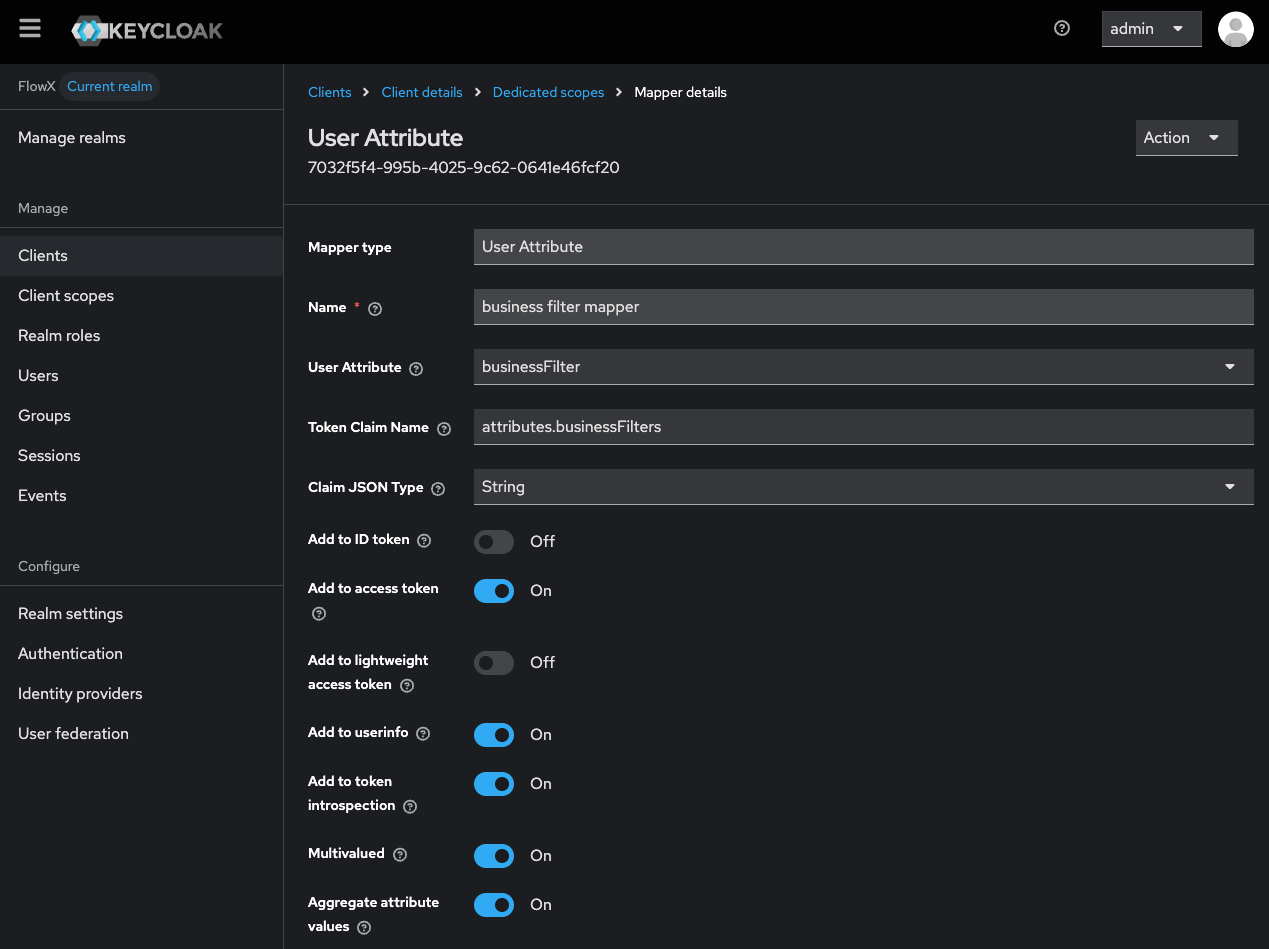
Business filters
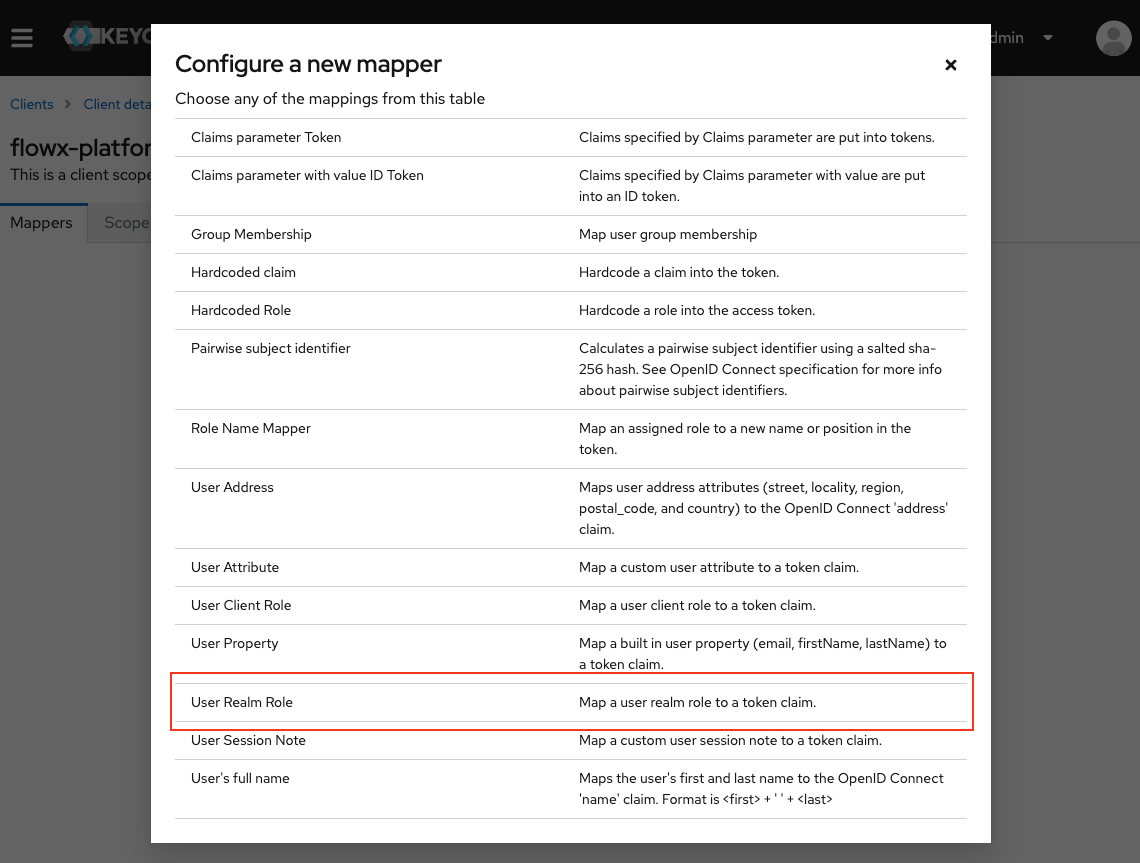
User realm role mapper
To add a roles mapper to the{your-client-name}-authenticate client, so roles will be available in the OAuth user info response, follow these steps:
Navigate to Client Scopes
{your-client-name}-authenticate-dedicated to open its settings.Ensure the Mappers tab is selected.Creating a basic client scope
To ensure consistent token configuration across all clients, you should create a default client scope named “basic” with predefined mappers.Navigate to Client Scopes
Configure Client Scope Settings
- Name: Enter
basic. - Type: Select Default.
- Protocol: Select OpenID Connect.
- Display on consent screen: Toggle OFF.
- Include in token scope: Toggle ON.
Add Predefined Mappers
-
sub mapper:
- Click Add mapper → From predefined mappers
- Select sub
- Click Add
-
auth_time mapper:
- Click Add mapper → From predefined mappers
- Select auth_time
- Click Add
Assign to All Clients
- Navigate to Clients in the left menu
- For each client (e.g.,
flowx-platform-authenticate,flowx-platform-authorize, and all service accounts):- Open the client settings
- Go to the Client Scopes tab
- Click Add client scope
- Select basic from the list
- Choose Default as the assignment type
- Click Add
Examples
Login
To request a login token:Refresh token
To refresh an existing token:User info
To retrieve user information:Adding service accounts
Admin service account
The admin service account is used by the admin microservice to connect with Keycloak, enabling user and group management features within the FlowX.AI Designer. Steps to add an Admin service account:Create the Client
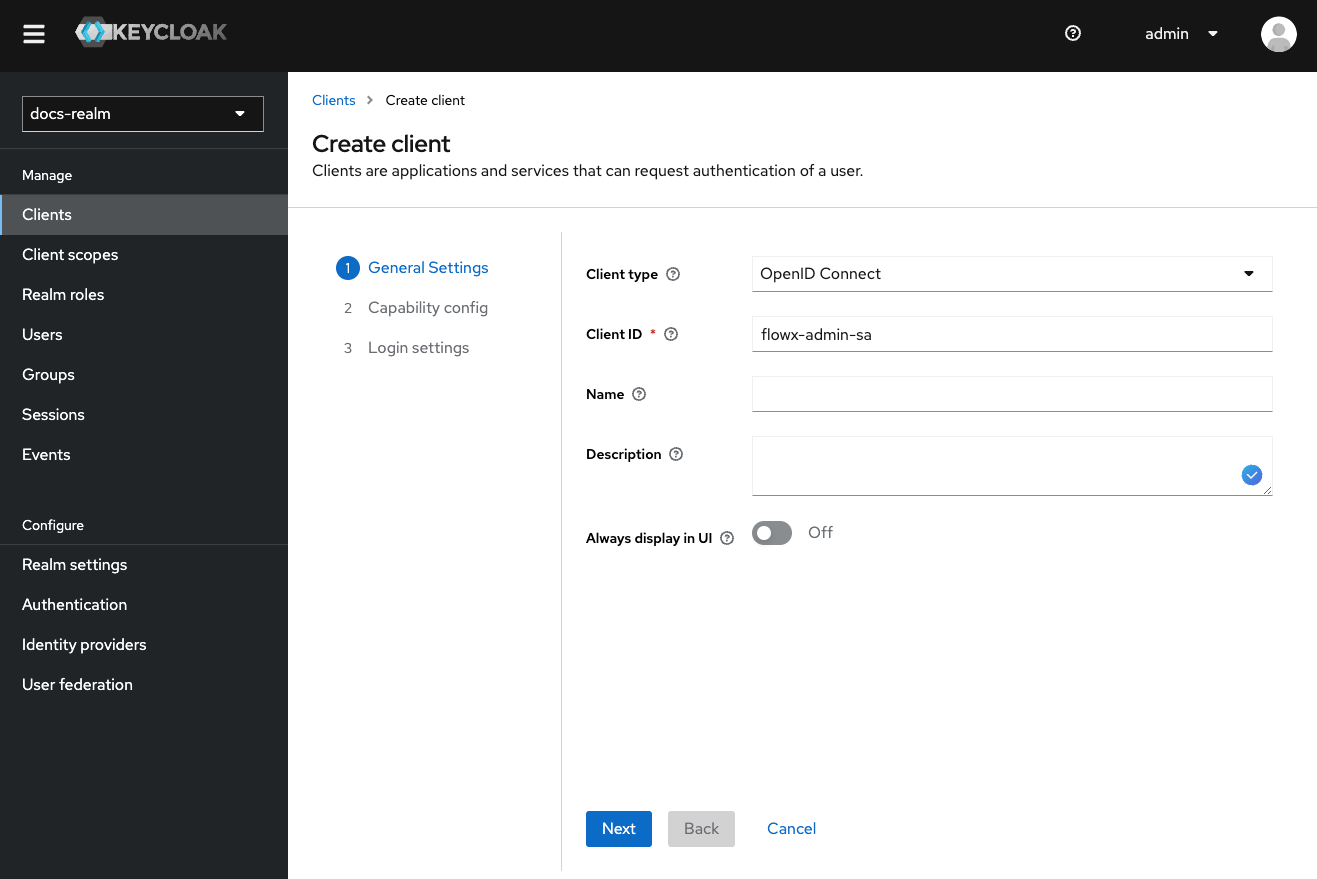
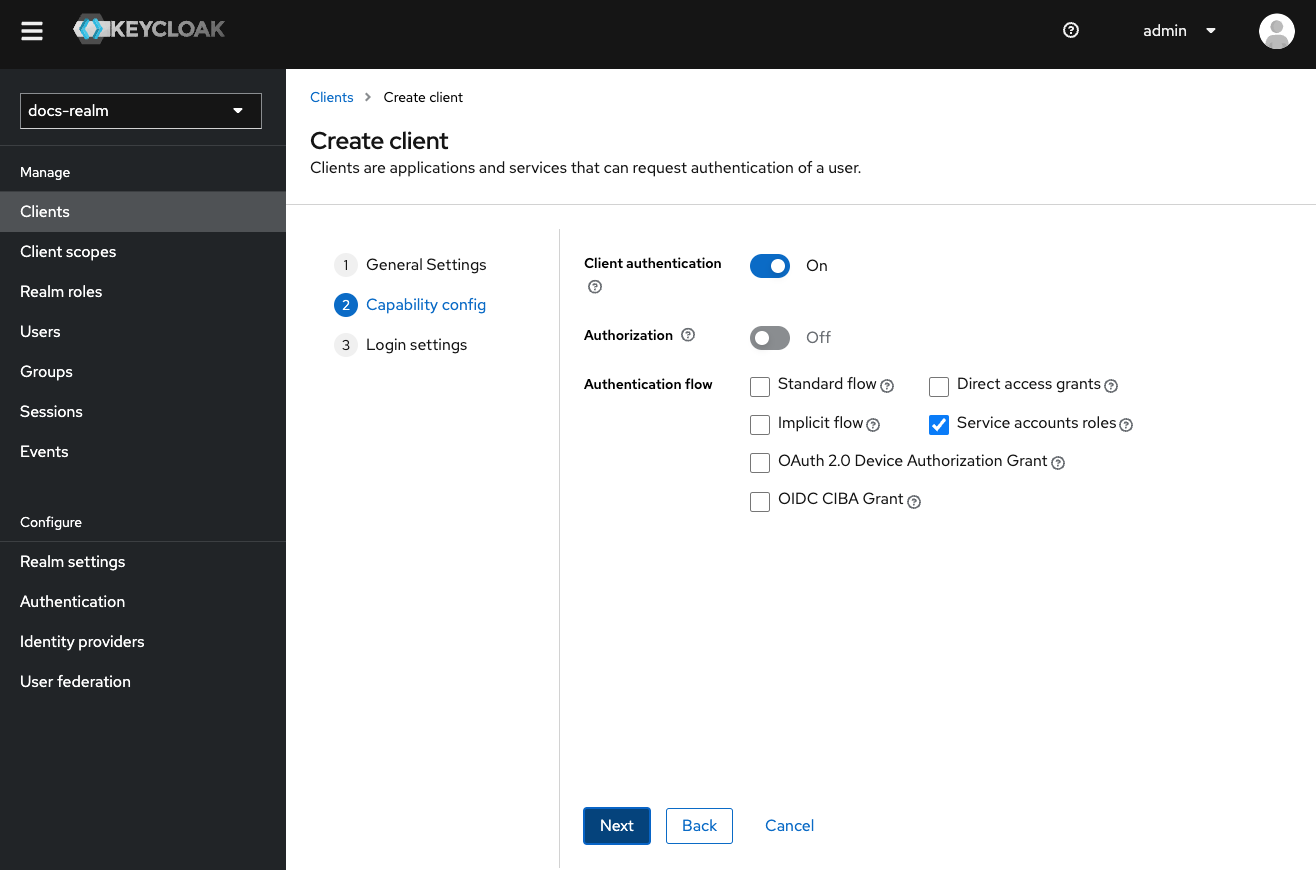
Configure Capability Config
- Enable Client authentication (access type).
- Disable Standard flow.
- Disable Direct access grants.
- Enable Service accounts roles.
Configure Additional Settings
- Backchannel Logout Session Required: Toggle OFF.
- Front Channel Logout: Toggle OFF.
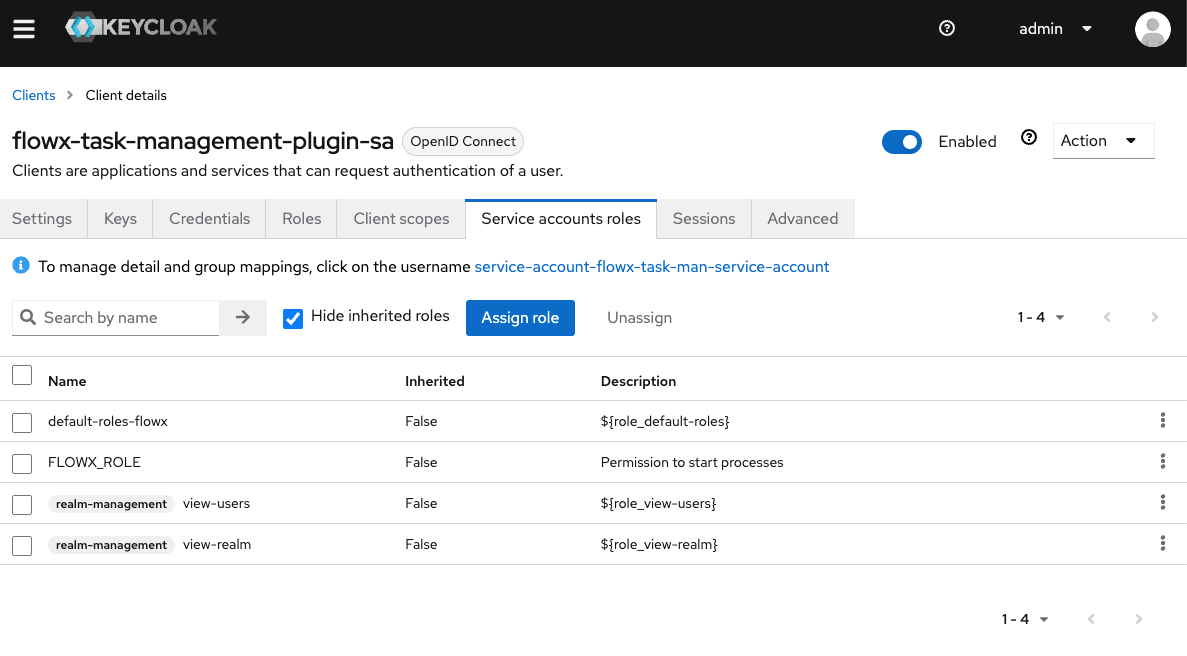
Task Management service account
The task management service account facilitates process initiation and enables the use of the task management plugin (requiring theFLOWX_ROLE and role mapper), and access data from Keycloak.
Steps to Add a Task Management service account:
Create the Service Account
Assign Necessary Roles
- view-users
- query-users
- query-groups
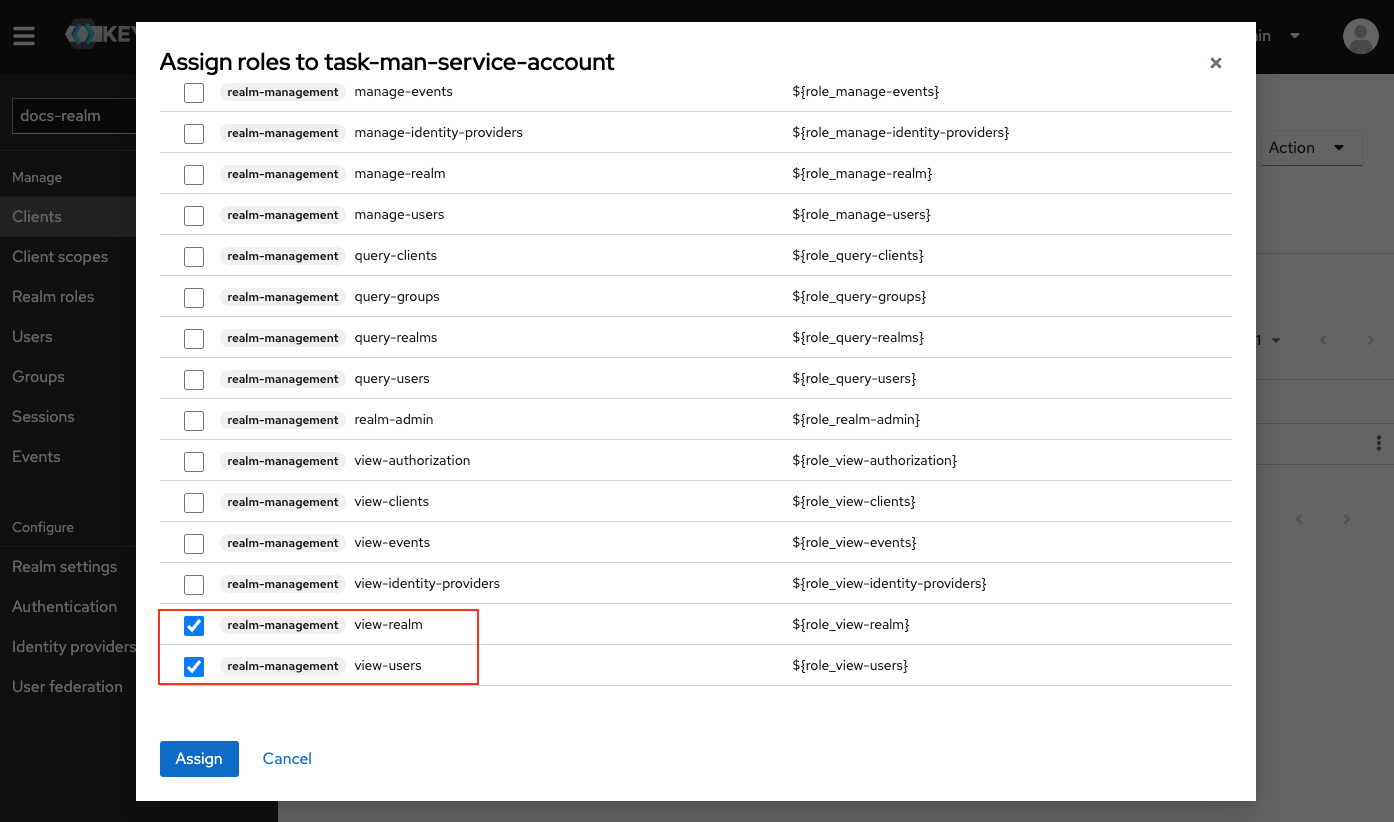
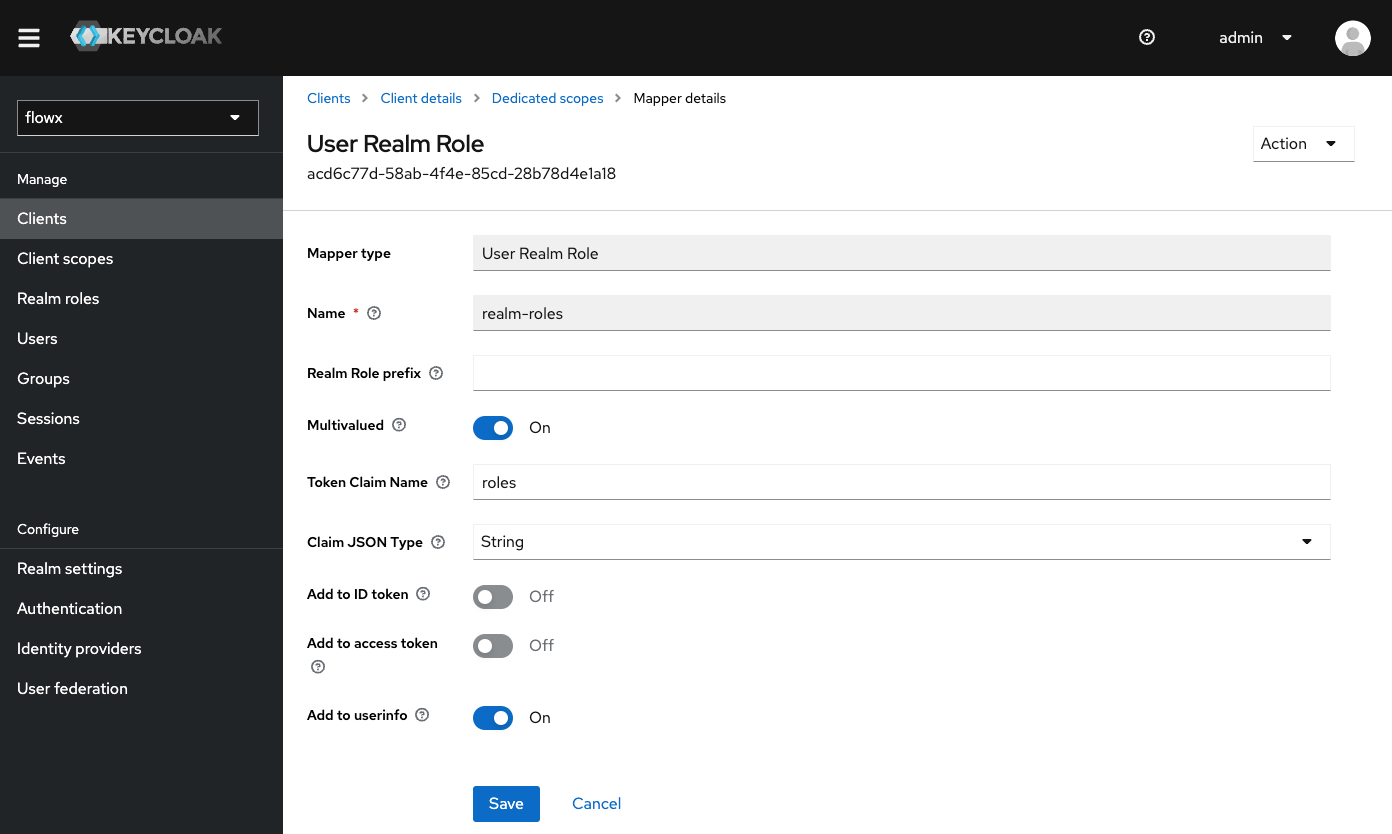
Add a Realm Roles Mapper
{your-client-name}-service-account to open its settings.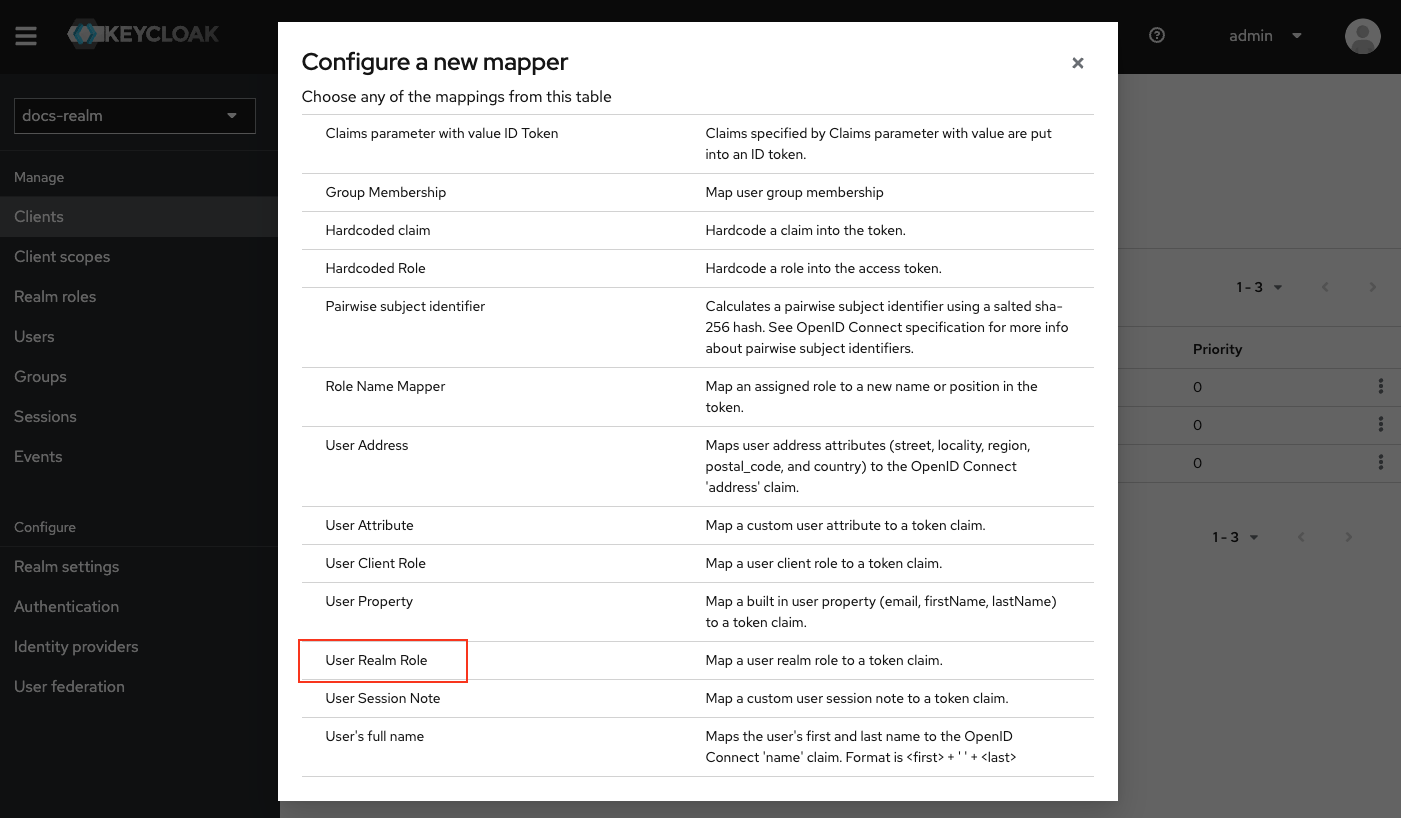
Configure the Mapper
realm-roles.Token Claim Name: Set it to roles.Disable Add to ID token.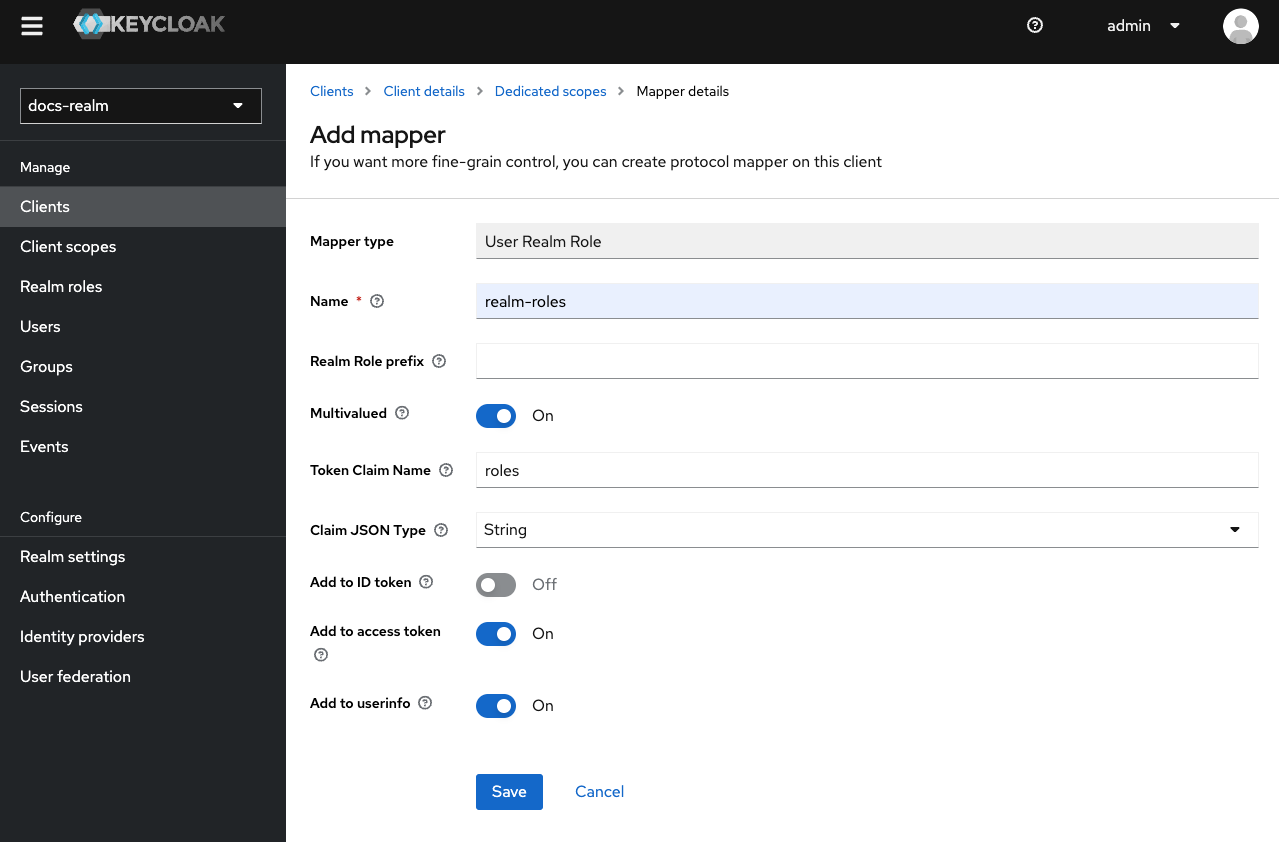
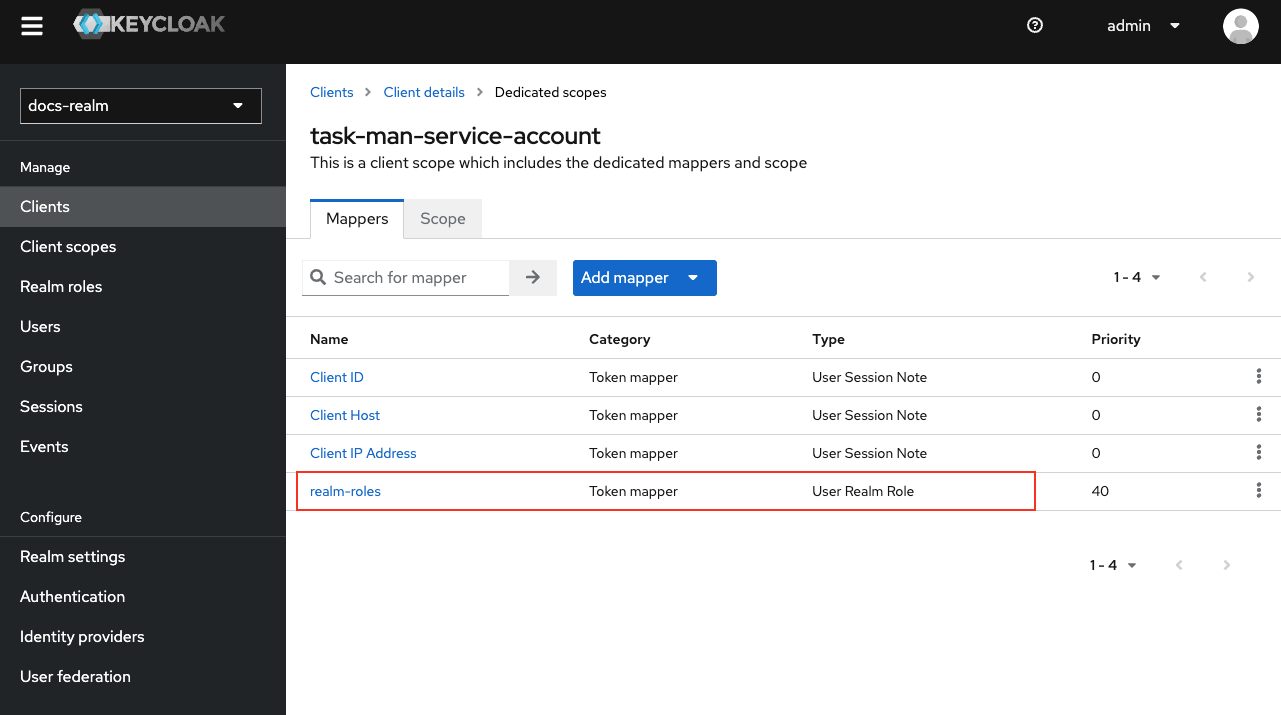
Add the Service Account Realm Role
FLOWX_ROLE service account realm role (used to grant permissions for starting processes).FLOWX_ROLE is used to grant permissions for starting processes in the FlowX.AI Designer platform. By default, this role is named FLOWX_ROLE, but its name can be changed from the application configuration of the Engine by setting the following environment variable:FLOWX_PROCESS_DEFAULTROLESProcess engine service account
The process engine requires a process engine service account to make direct calls to the Keycloak API.Create the Client
Assign Service Account Client Roles
Add a Realm Roles Mapper
{your-client-name}-service-account to open its settings.Ensure the Mappers tab is selected within the dedicated client scope.Click Add mapper. From the list of available mappers, select User Realm Role.Configure the mapper:- Name: Enter
realm-roles - Token Claim Name: Set it to
roles - Add to ID token: Toggle OFF
- Add to token introspection: Toggle ON
Scheduler service account
Create the Client
Assign Service Account Client Roles
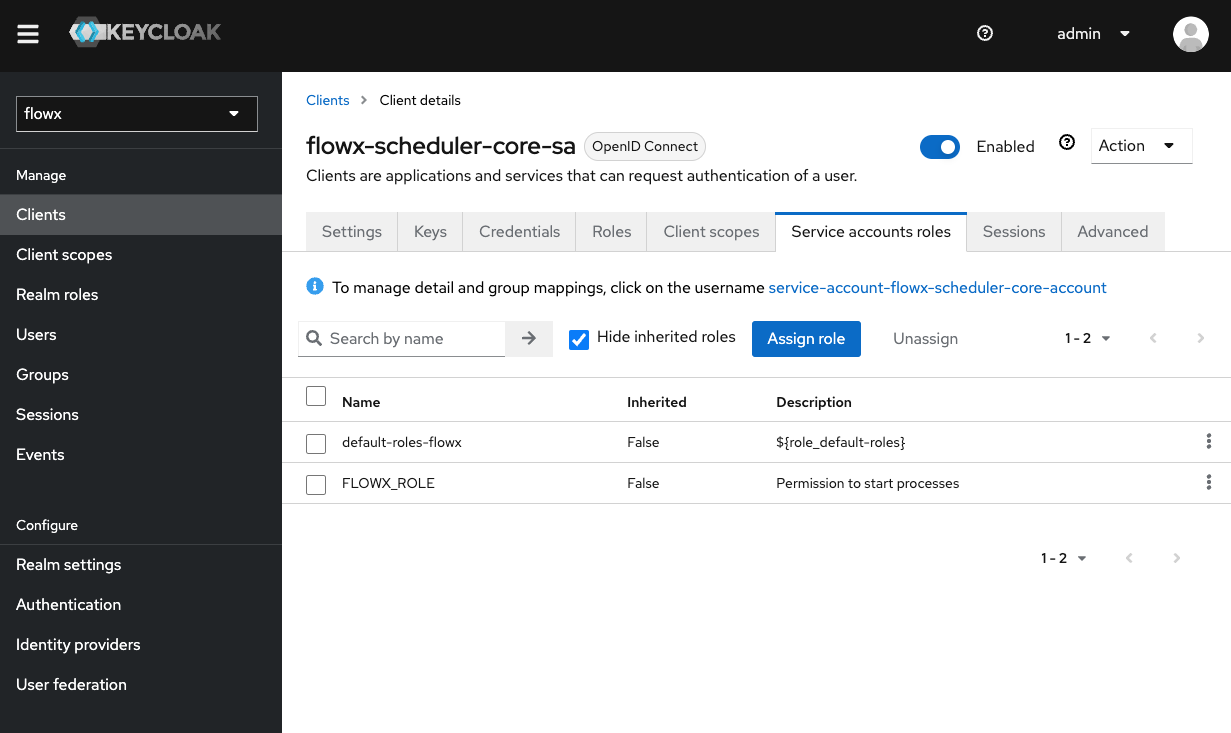
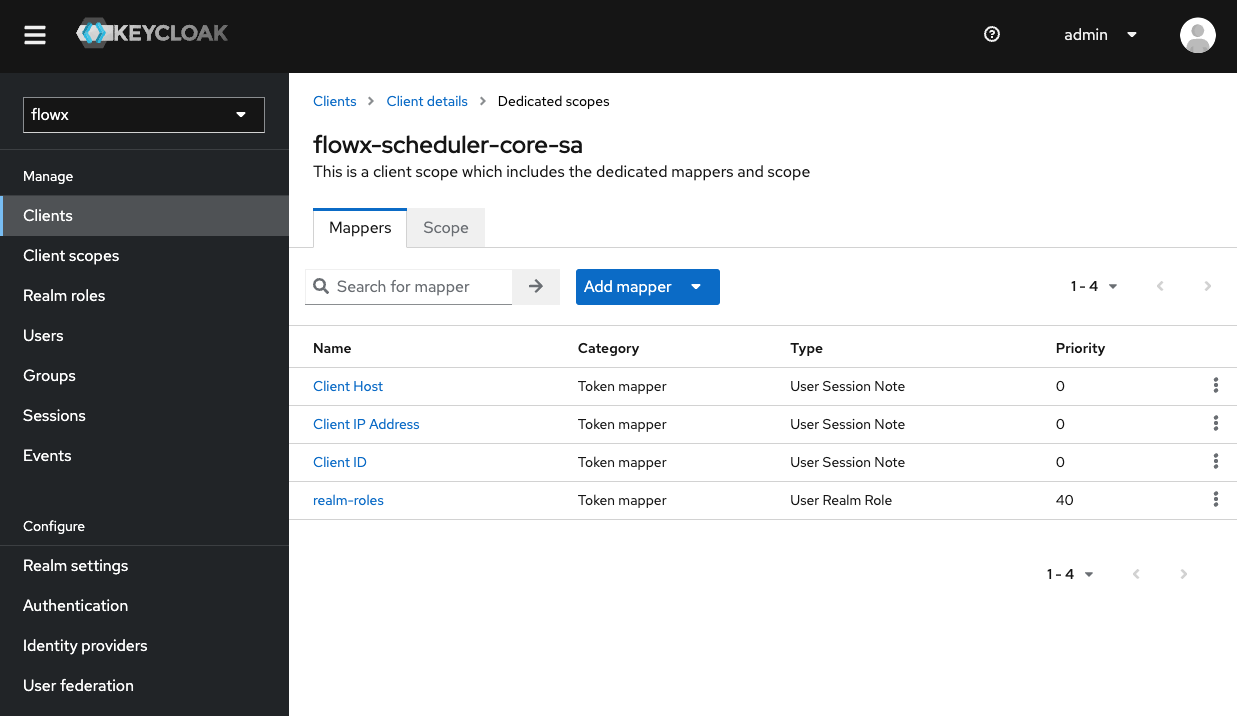
Add a Realm Roles Mapper
{your-client-name}-service-account to open its settings.Ensure the Mappers tab is selected within the dedicated client scope.Click Add mapper. From the list of available mappers, select User Realm Role.Configure the mapper:- Name: Enter
realm-roles - Token Claim Name: Set it to
roles - Add to ID token: Toggle OFF
- Add to token introspection: Toggle ON
Integration Designer service account
The Integration Designer service account is used by the integration designer microservice to interact securely with Keycloak, enabling it to manage various integrations within the FlowX.AI platform. Steps to set up an Integration Designer service account:Create the Client
- In Keycloak, navigate to Clients and select Create client.
- Enter a Client ID for your new client (e.g.,
flowx-integration-designer-sa).
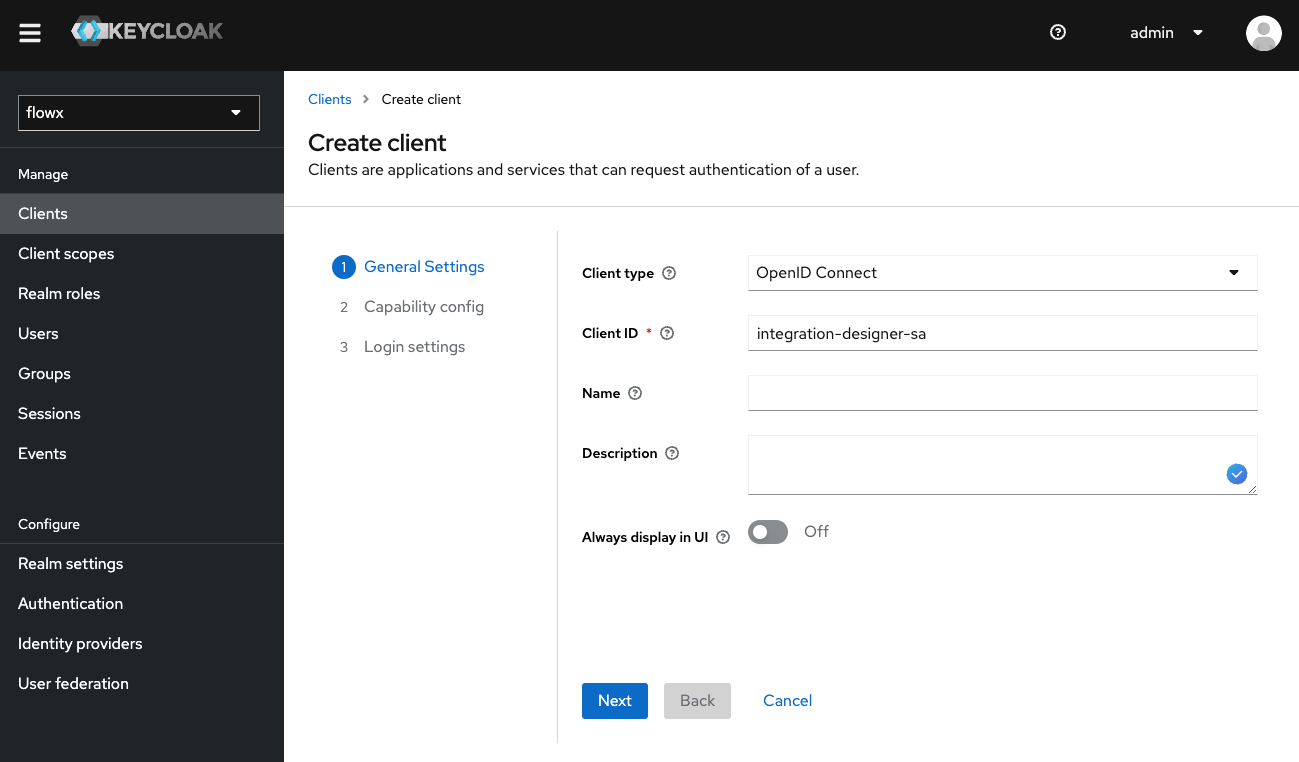
Configure Client Capabilities
- Enable Client authentication under access type.
- Enable Service accounts roles to allow the account to manage integrations.
Assign Service Account Client Roles
Authorization System service account
The Authorization System service account is used for managing user authentication and authorization operations, including user management, realm configuration, and access control within the FlowX.AI platform. Steps to set up an Authorization System service account:Create the Client
flowx-authorization-system-sa).Configure Capability Config
- Enable Client authentication (access type).
- Disable Standard flow.
- Disable Direct access grants.
- Enable Service accounts roles.
Configure Additional Settings
- Backchannel Logout Session Required: Toggle OFF.
- Front Channel Logout: Toggle OFF.
Assign Service Account Client Roles
- view-users
- query-users
- manage-users
- manage-realm
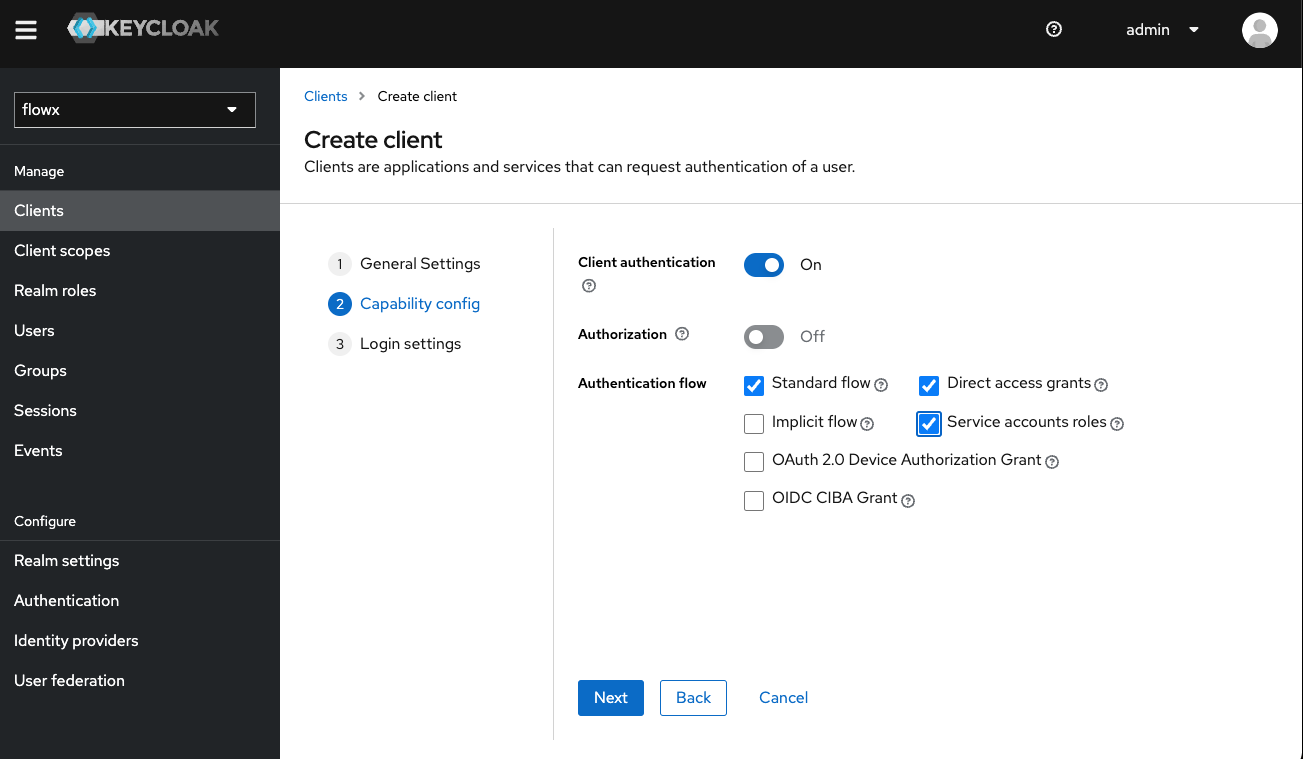
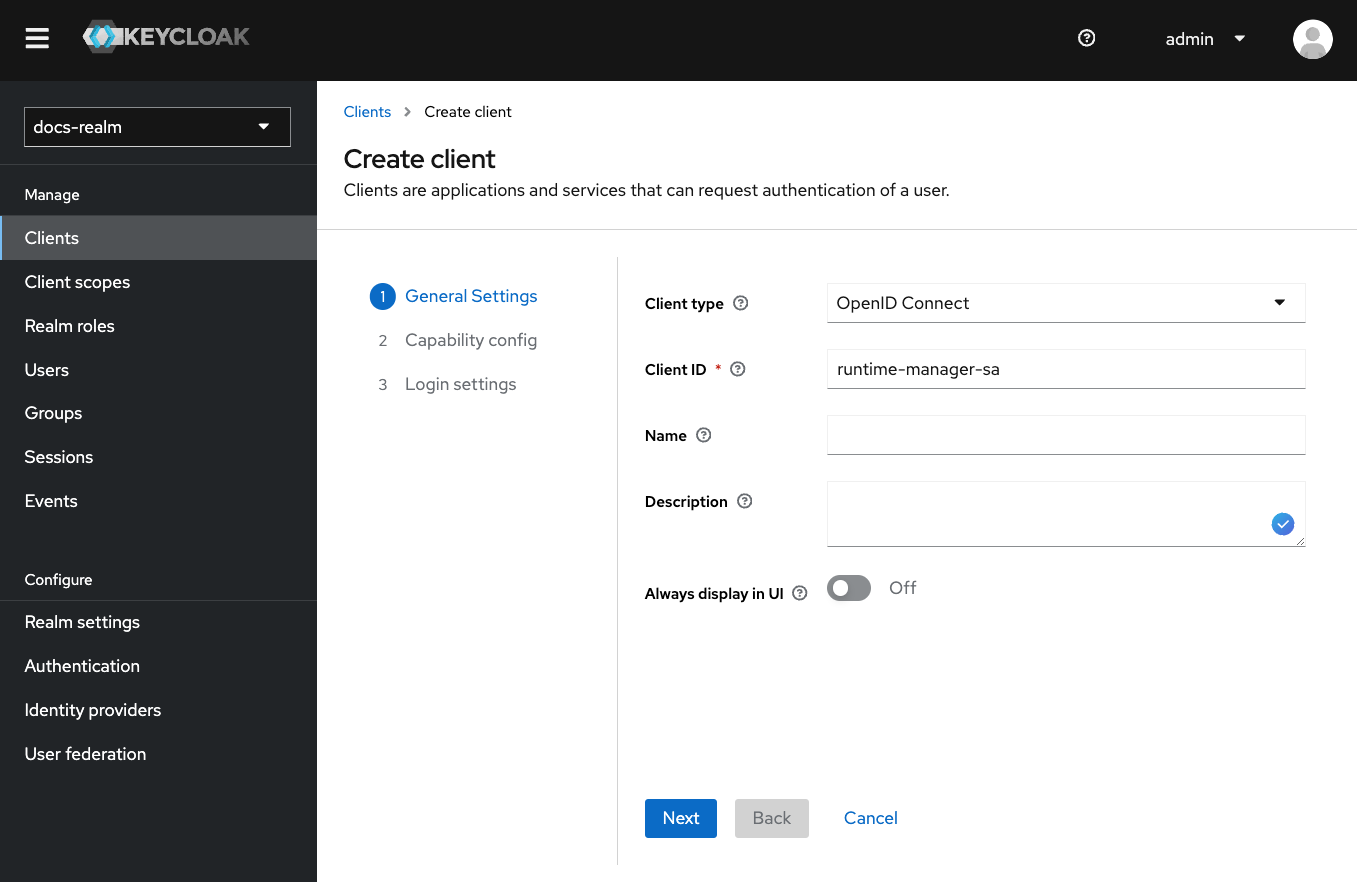
Runtime manager service account
The runtime manager service account is used by both Application Manager and Runtime Manager services to connect with Keycloak and perform export/import operations for builds, application versions, or other resource-specific tasks. Steps to add a Runtime manager service account:Create the Client
Configure Capability Config
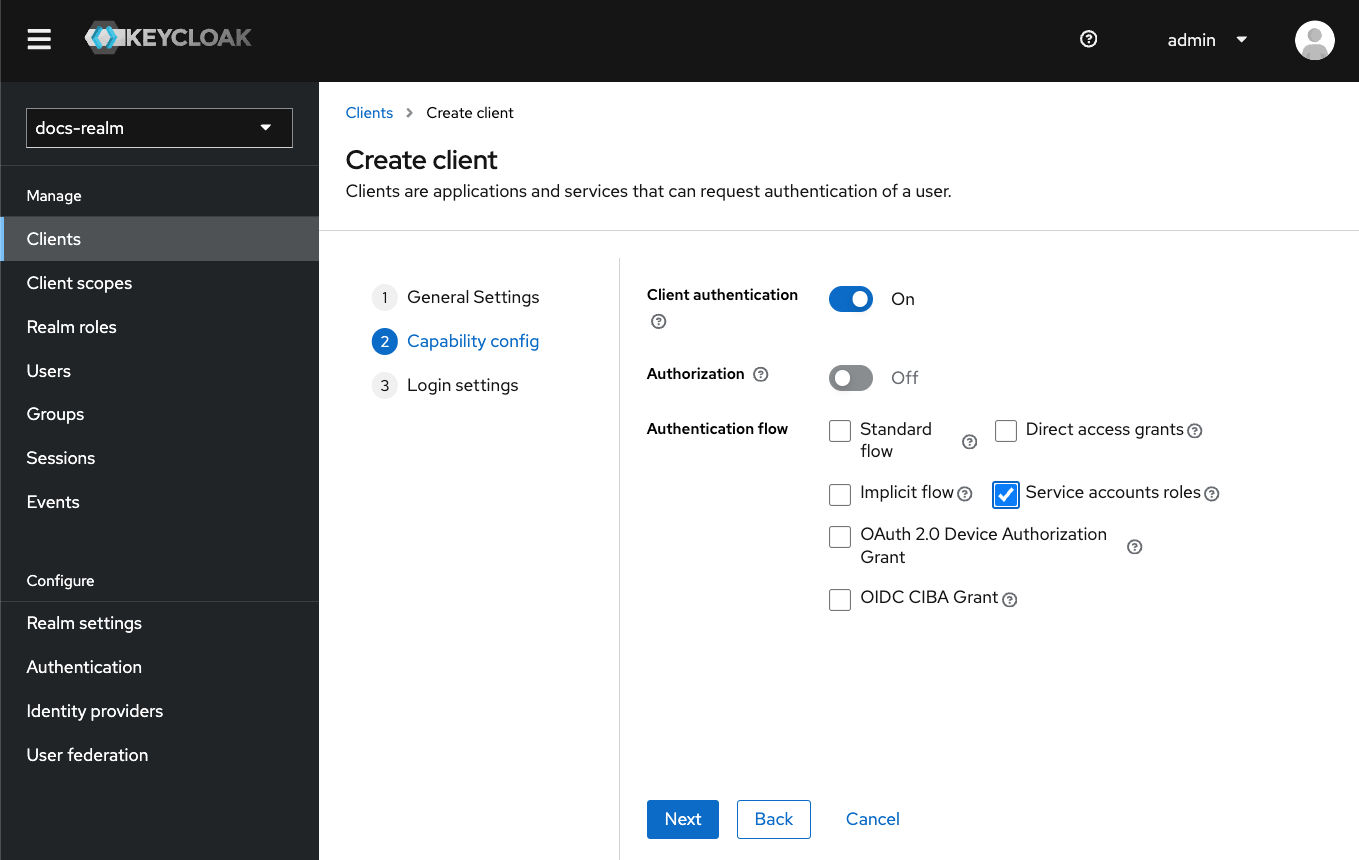
- Enable Client authentication (access type).
- Disable Standard flow.
- Disable Direct access grants.
- Enable Service accounts roles.
Configure Additional Settings
- Backchannel Logout Session Required: Toggle OFF.
- Front Channel Logout: Toggle OFF.

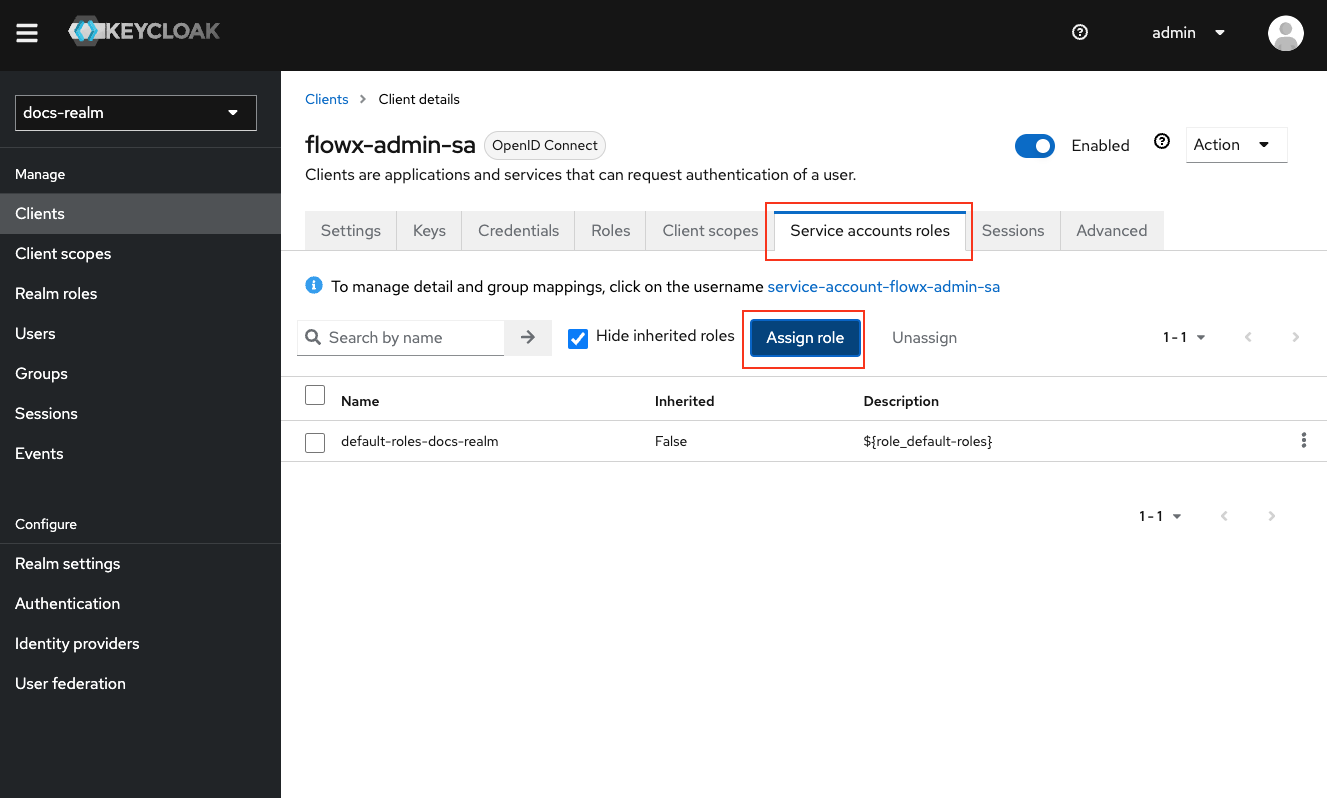
Configure Service Account Roles
Configuring SA_FLOWX realm role
TheSA_FLOWX role is a realm-level role that should be assigned to all service accounts to ensure proper authentication and authorization across the FlowX.AI platform.
Create the SA_FLOWX Realm Role
- In the Keycloak admin console, navigate to Realm roles in the left menu.
- Click Create role.
- Enter
SA_FLOWXas the Role name. - Add a description: “Service account role for FlowX.AI platform services”.
- Click Save.
Assign SA_FLOWX to Service Accounts
SA_FLOWX realm role:- process-engine
- flowx-admin-sa
- runtime-manager-sa
- flowx-integration-designer-sa
- scheduler-core
- nosql-db-runner-sa
- flowx-authorization-system-sa
- task-manager (if applicable)
- Navigate to Clients and select the service account client.
- Go to the Service accounts roles tab.
- Click Assign role.
- In the Filter field, select Filter by realm roles.
- Find and select SA_FLOWX from the list.
- Click Assign.
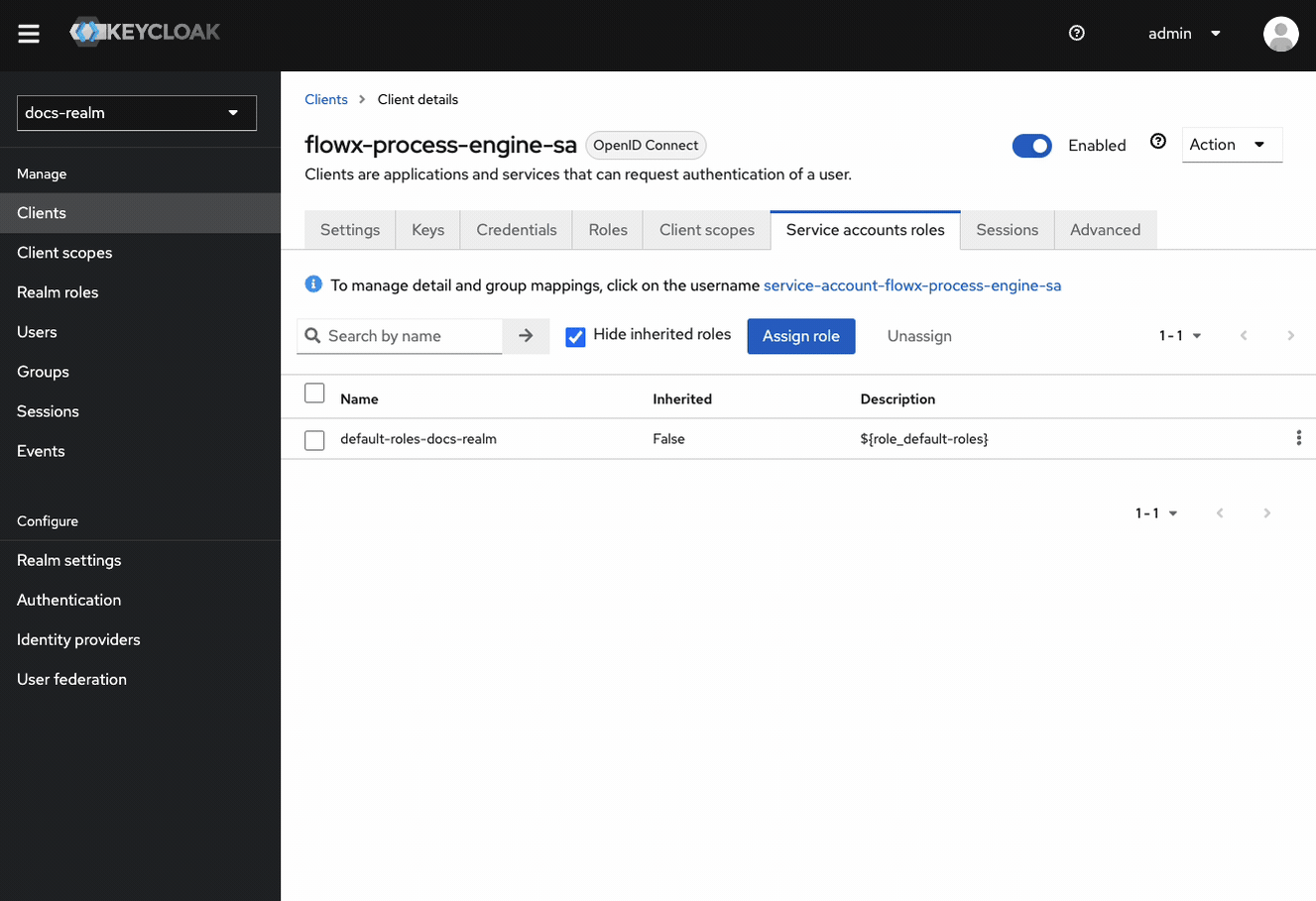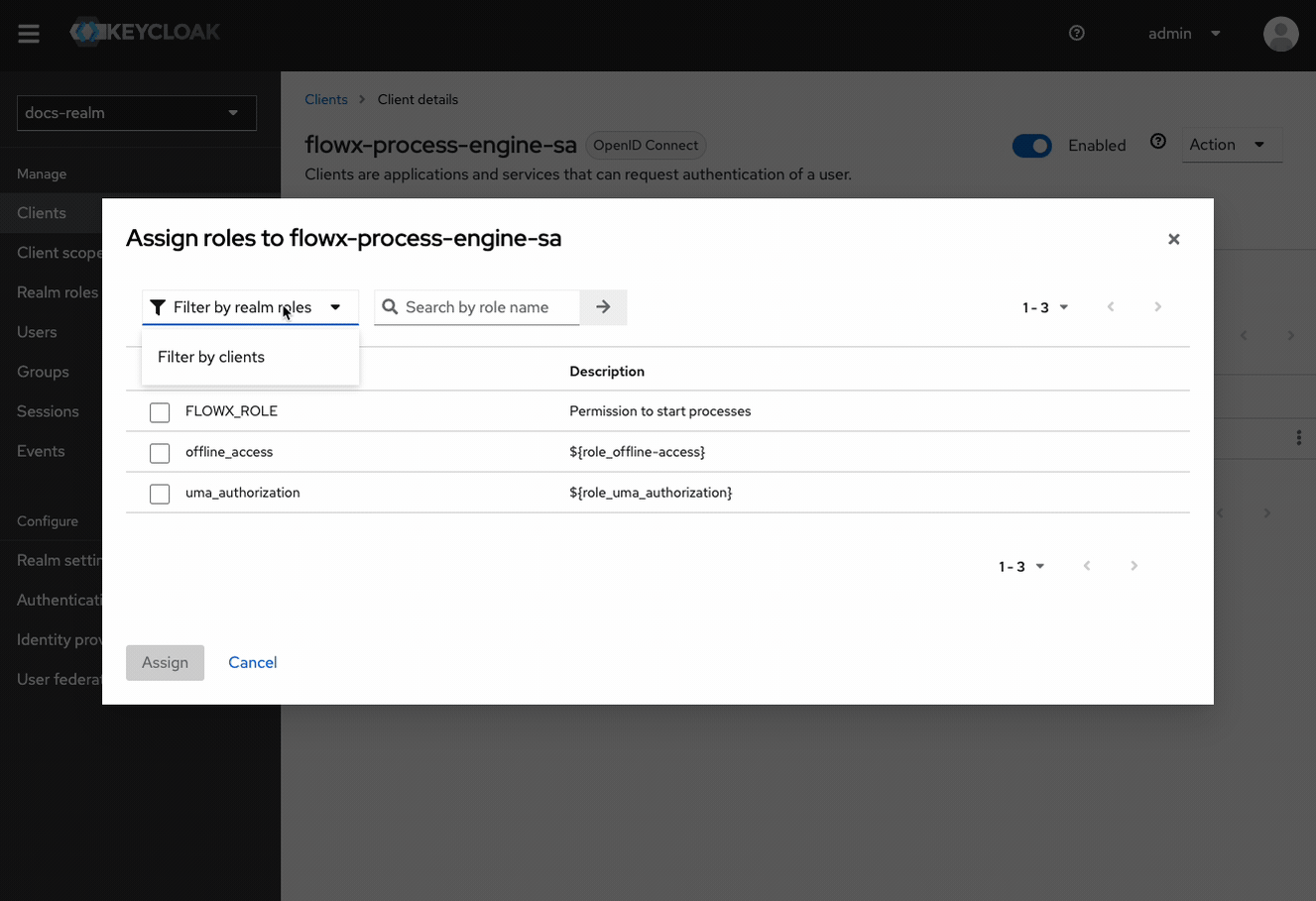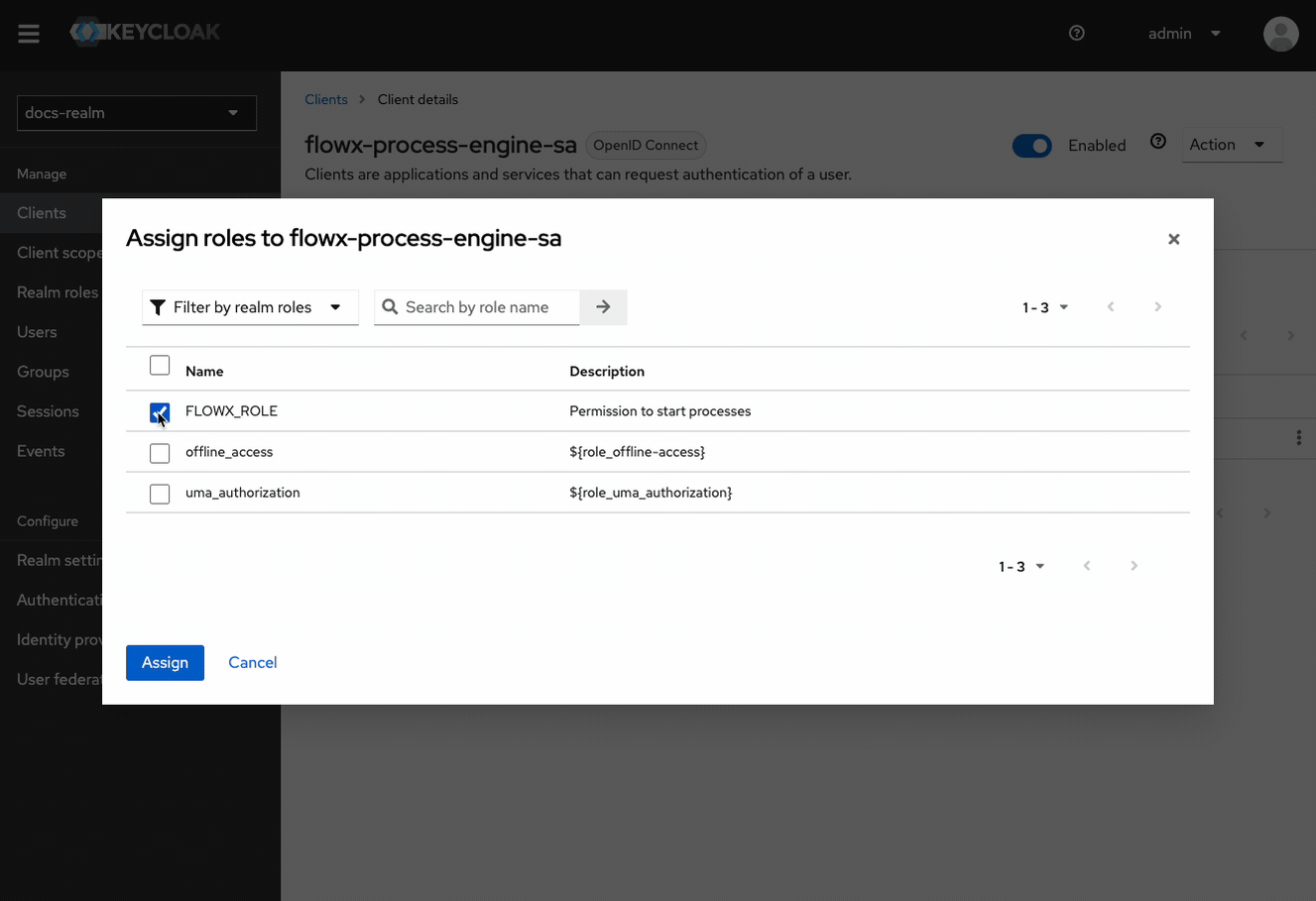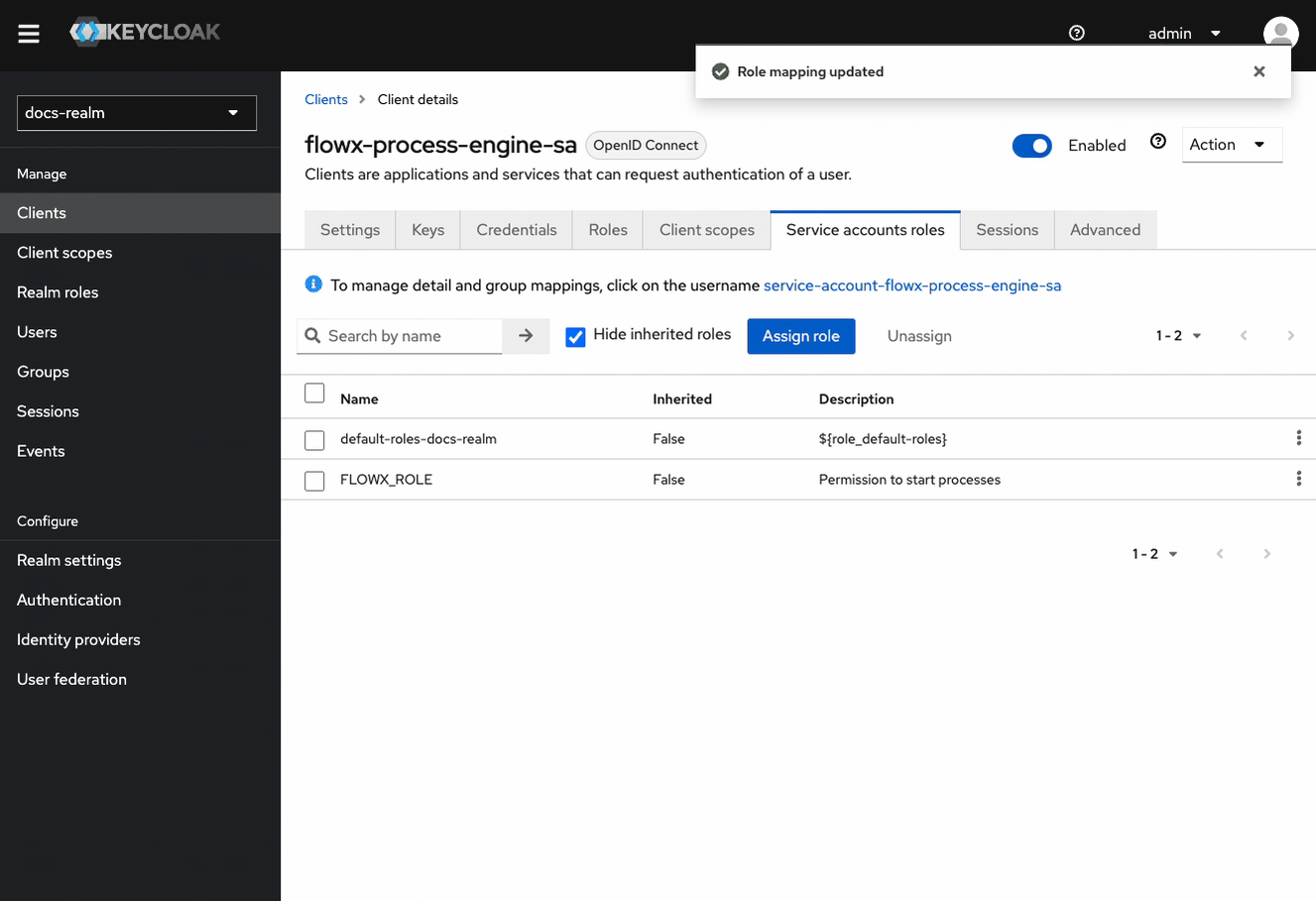
Verify Role Assignment
SA_FLOWX role listed in its Service accounts roles tab.SA_FLOWX role ensures consistent authentication and authorization behavior across all FlowX.AI platform services. Make sure all service accounts have this role assigned for proper system operation.