Access to a process definition
Setting up user role-based access on process definitions is done by configuring swimlanes on the process definition.Swimlanes
To be able to access the roles defined in the identity provider solution, a service account with appropriate permissions needs to be added in the identity provider. And the details of that service account need to be set up in the platform configuration.
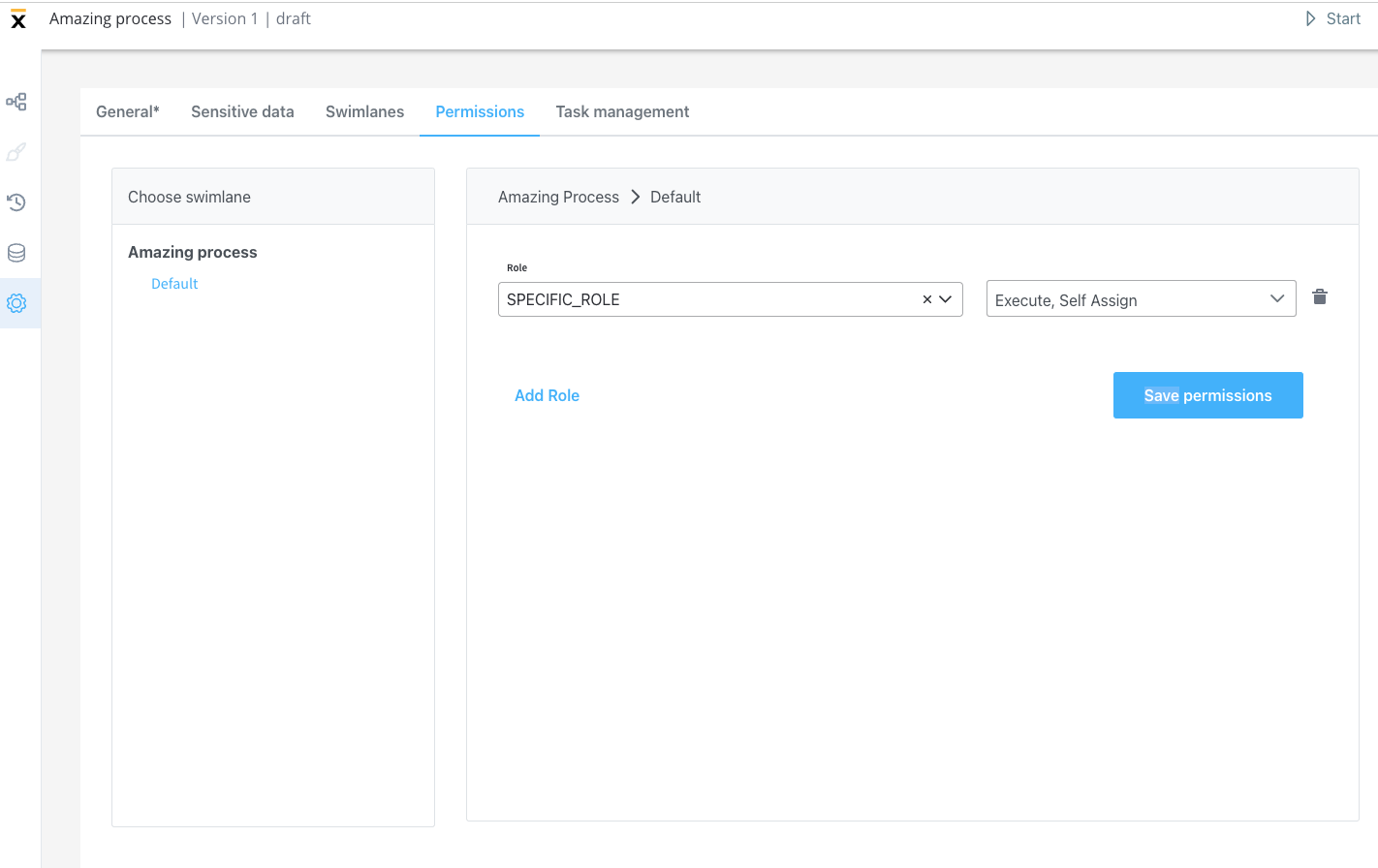
- execute - the user will be able to start process instances and run actions on them
- self-assign - the user can assign a process instance to them and start working on it
This is valid for > 2.11.0 FLOWX.AI platform release.
- view - the user will be able to view process instance data
- assign - user can assign tasks to other users (this operation is only accessible through the Task management plugin)
- unassign - user can unassign tasks from other users (this operation is only accessible through the Task management plugin)
- hold - user can mark the process instance as on hold (this operation is only accessible through the Task management plugin)
- unhold - user can mark the process instance as not on hold (this operation is only accessible through the Task management plugin)
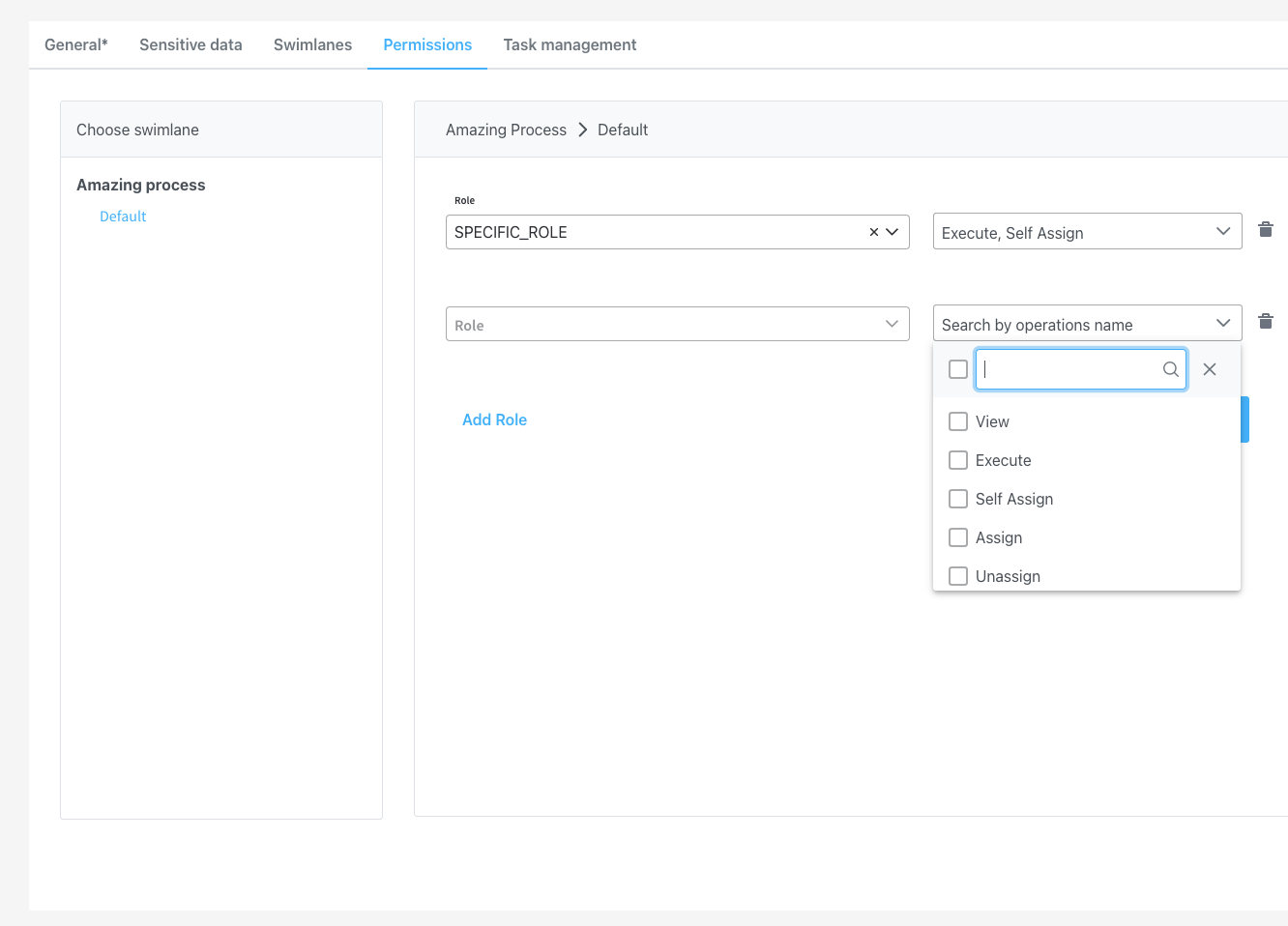
Configuration examples
Valid for < 2.11.0 release version.
Regular user
Below you can find an example of configuration of roles for a regular user: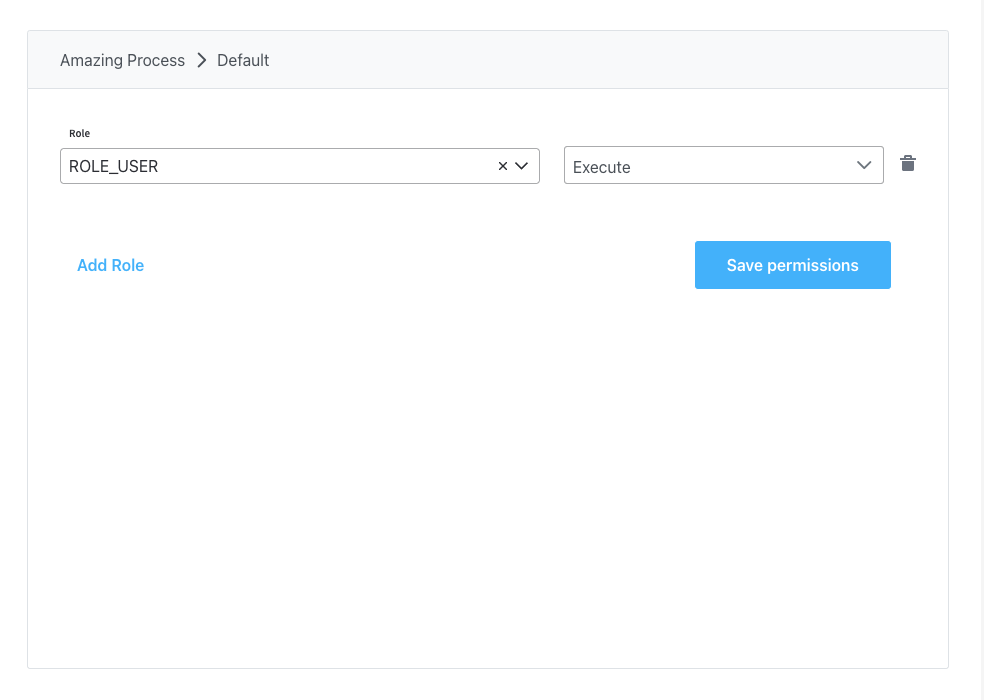
Admin
Below you can find an example of configuration of roles for an admin user: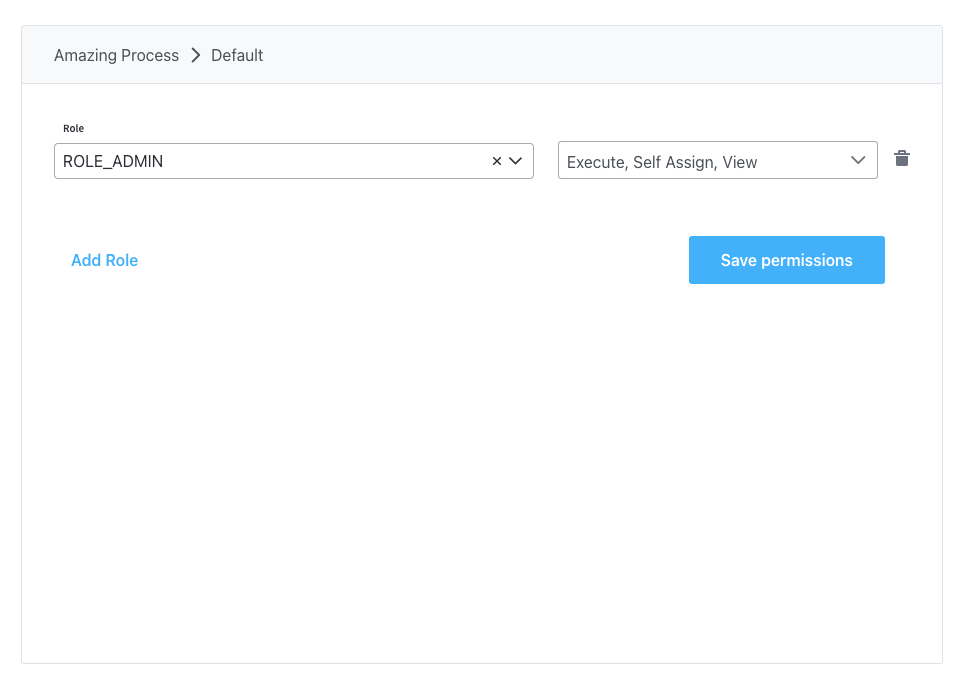 After setting up your preferred identity provider solution, you will need to add the desired access roles in the application configuration for the FLOWX Engine (using environment variables):
Authorization & access roles
After setting up your preferred identity provider solution, you will need to add the desired access roles in the application configuration for the FLOWX Engine (using environment variables):
Authorization & access roles
Restricting process instance access based on business filters
Business filters Before they can be used in the process definition the business filter attributes need to be set in the identity management platform. They have to be configured as a list of filters and should be made available on the authorization token. Application users will also have to be assigned this value.Viewing processes instances
Active process instances and their related data can be viewed from the FLOWX Designer. A user needs to be assigned to a specific role in the identity provider solution to be able to view this information. By default, this role is namedFLOWX_ROLE, but its name can be changed from the application configuration of the Engine by setting the following environment variable:
FLOWX_PROCESS_DEFAULTROLES
When viewing process instance-related data, it can be configured whether to hide specific sensitive user data. This can be configured using the FLOWX_DATA_ANONYMIZATION environment variable.