Recommended Keycloak setup
To configure a minimal required Keycloak setup, follow these steps:- Create a new realm
- Define available roles and realm-level roles assigned to new users.
- Create/import user roles and groups
- Create new users
- Add clients
- Configure access type, valid redirect URIs, and enable necessary flows.
- Add role mappers
- Add service accounts
- Set up admin, task management, and process engine service accounts.
Recommended keycloak version: 18.0.x
Keycloak documentation
Creating a new realm
A realm is a space where you manage objects, including users, applications, roles, and groups. To create a new realm:- Log in to the Keycloak Admin Console using the appropriate URL for your environment (e.g., QA, development, production).
- In the top left corner dropdown menu, click Add Realm.
If you are logged in to the master realm this dropdown menu lists all the realms created. The Add Realm page opens.
- Enter a realm name and click Create.

- Configure the realm settings (Realm Settings → Tokens), such as SSO session idle and access token lifespan, according to your organization’s needs:
- SSO Session idle - suggested: 30 Minutes
- Access Token Lifespan - suggested: 30 Minutes

Creating/importing user groups and roles
You can either create or import a user group into a realm. We prepared a script that helps you to import a super admin group provided with the necessary default user roles. You can create or import user groups into a realm. If you choose to import, follow the provided script to import a super admin group (SUPER_ADMIN_USERS) with default user roles. After importing, add an admin user to the group and assign the necessary roles.
Make sure to validate the imported roles by checking the following section:
Default roles
Creating new users
To create a new user in a realm and generate a temporary password:- In the left menu bar, click Users to open the user list page.
- On the right side of the empty user list, click Add User.
- Fill in the required fields, including the username, and ensure Email Verified is set to ON.
- In the Groups field, choose a group from the dropdown menu, in our case:
FLOWX_SUPER_USERS.

- Save the user, go to the Credentials tab, and set a temporary password.

Adding clients
A Client represents an instance of an application. A client is attached to a specific realm. First, addplatform-authenticate client - will be used for login/logout/refresh token by web and mobile apps.
- Click Clients in the top left menu, then click Create.
- Set a client ID as
{example}-authenticate, which will be used for login, logout, and refresh token operations. - Set the Client Protocol type as
openid-connect.

- Open the newly created client and edit the following properties:
- Set Access type to public (this will not require a secret).
- Set Valid redirect URIs, specifying a valid URI pattern that a browser can redirect to after a successful login or logout, simple wildcards are allowed.
- Enable Direct Access Grants and Implicit Flow Enabled by setting them to ON.

- Add mappers to
{example}-authenticateclient.
Refer to the next section on how to add mappers and which mappers to clients.
Adding protocol mappers
Protocol mappers in Keycloak allow for the transformation of tokens and documents, enabling actions such as mapping user data into protocol claims or modifying requests between clients and the authentication server. To enhance your clients, consider adding the following mappers:- Group Membership mapper -
realm-groups: This mapper can be utilized to map user groups to the authorization token. - User Attribute mapper -
business filter mapper: Use this mapper to map custom attributes, for example, mapping the businessFilters list, to the token claim. - User Realm role -
realm-roles: This mapper enables mapping a user’s realm role to a token claim.
Group Membership mapper
To add a group membership mapper:- Navigate to Clients and select your desired client, in our case,
{example}-authenticate - Go to the Mappers tab and click Create to create a new mapper.
- Provide a descriptive Name for the mapper to easily identify its purpose.
- Select Group Membership as the mapper type.
- Set the token claim name for including groups in the token. In this case, set it as
groups.
 By configuring the group membership mapper, you will be able to include the user’s group information in the token for authorization purposes.
By configuring the group membership mapper, you will be able to include the user’s group information in the token for authorization purposes.
User Attribute mapper
To include custom attributes such as business filters in the token claim, you can add a user attribute mapper with the following settings:- Go to the desired client,
{example}-authenticate, and navigate to the Mappers section. - Click on Create to create a new mapper.
- Configure the following settings for the user attribute mapper:
- Mapper Type: User Attribute
- User Attribute: businessFilters
- Token Claim Name: attirubtes.businessFilters
- Add to ID token: OFF
- Multivalued: ON
 By adding this user attribute mapper, the custom attribute “businessFilters” will be included in the token claim under the name “attributes.businessFilters”. This will allow you to access and utilize the business filters information within your application.
You can find more information about business filters in the following section:
By adding this user attribute mapper, the custom attribute “businessFilters” will be included in the token claim under the name “attributes.businessFilters”. This will allow you to access and utilize the business filters information within your application.
You can find more information about business filters in the following section:
Business filters
User realm role
Add roles mapper to{example}-authenticate client - so roles will be available on the OAuth user info response.
To add a roles mapper, follow these steps:
- Go to the desired client,
{example}-authenticate, and navigate to the Mappers section. - Click on Create to create a new mapper.
- Configure the following settings for the user attribute mapper:
- Mapper Type: User Realm Role
- Token Claim Name: role
- Add to userinfo: ON

Examples
Login
Refresh token
User info
Authorizing client
Add{example}-platform-authorize client - it will be used to authorize rest requests to microservices and Kafka
- set Client Protocol to openid-connect
- set Access type as confidential
- disable Direct Access Grants Enabled - OFF
- Valid Redirect URIs - mandatory
- disable Backchannel Logout Session Required - OFF
{example}-platform-authorize client will be created and can be used to authorize REST requests to microservices and Kafka within your application.

Minimal auth config for microservices
Adding service accounts
What is a service account?A service account is an account that grants direct access to the Keycloak API for a specific component.Each client has a built-in service account which allows it to obtain an access token. To use this feature you must set the Access Type of your client to confidential. When you do this, the Service Accounts Enabled switch will appear.
Admin service account
The admin service account is employed by the admin microservice to establish a connection with Keycloak for the purpose of utilizing user and group management features within the designer.
- Add a new client by selecting Clients then click Create.

- Next, set Access type as confidential and enable Service Accounts.

- Go to Clients → realm-management → Roles and add the following service account client roles under realm-management:
- manage-realm
- manage-users
- query-users
Make sure first that you created a realm-management client with the following client roles: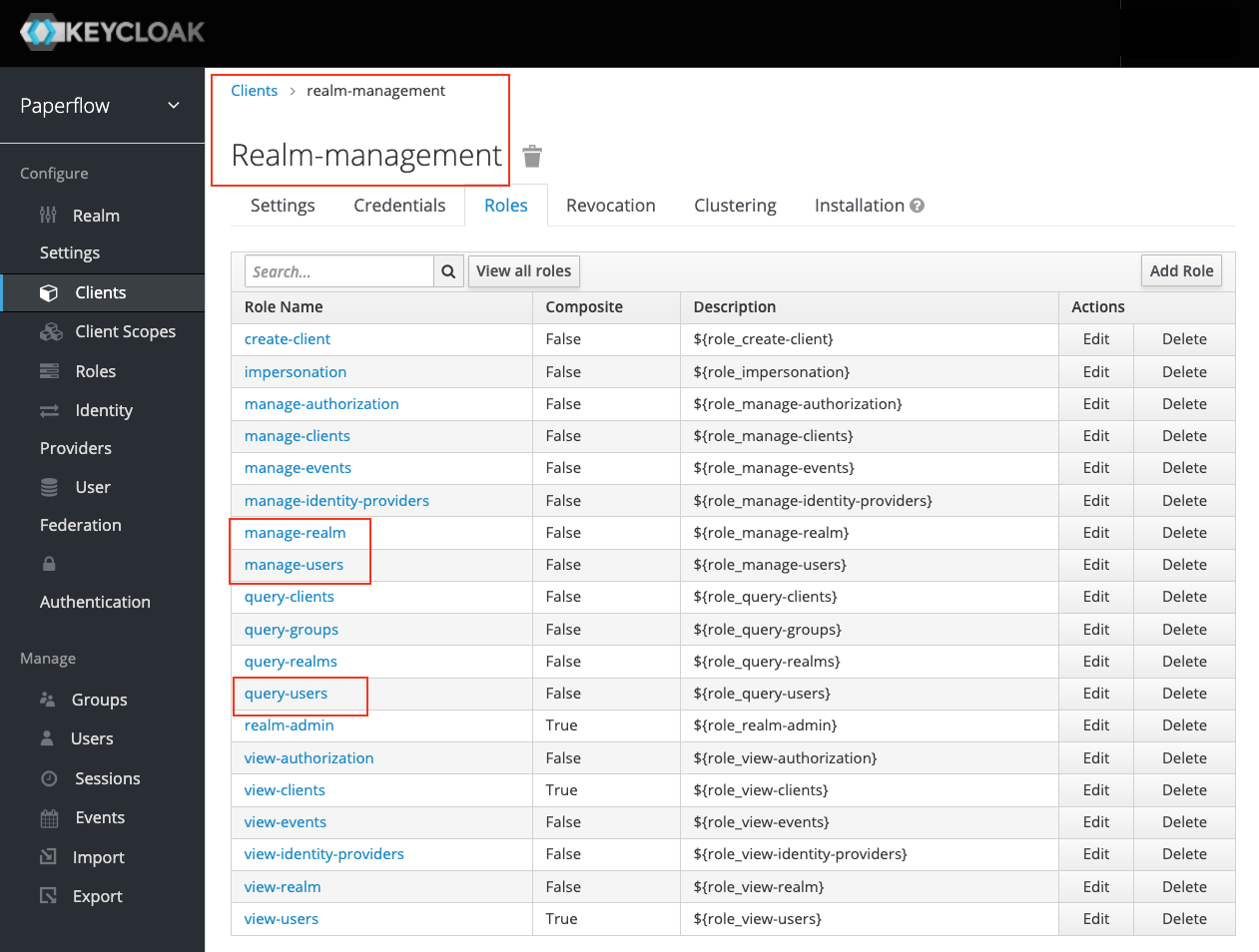

- Assign the necessary service account roles:
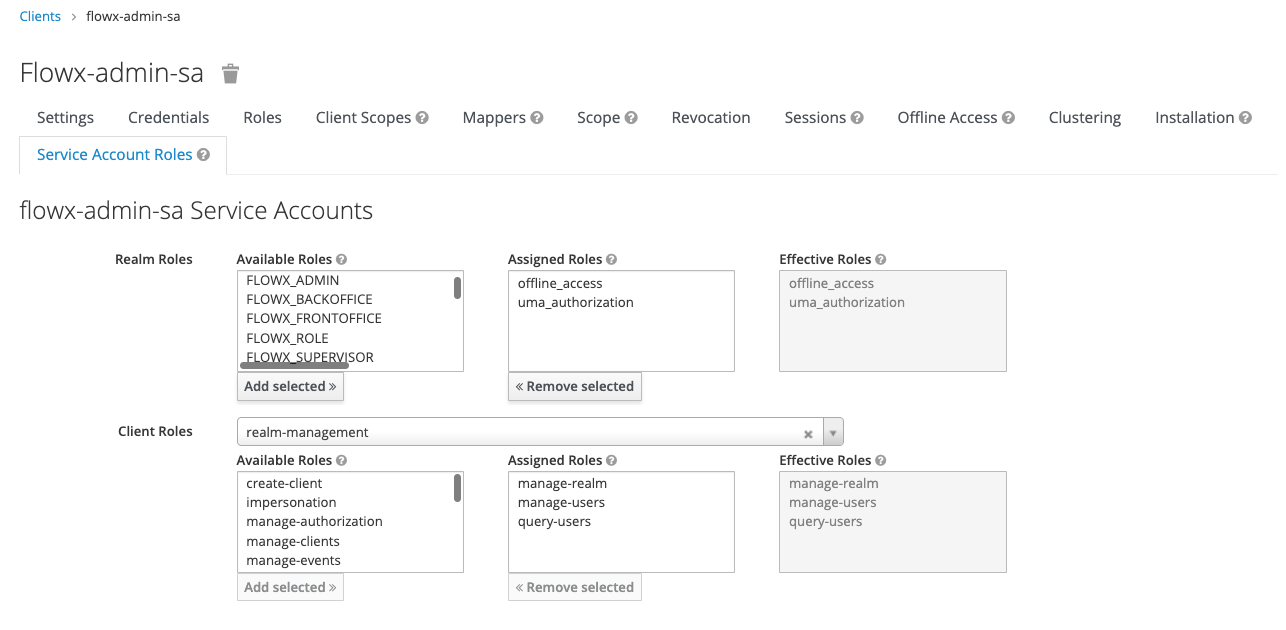 In the provided example, the admin service account can have the following assigned roles, depending on the required access scopes:
In the provided example, the admin service account can have the following assigned roles, depending on the required access scopes:
- manage-users
- query-users
- manage-realm
The admin service account does not require mappers as it doesn’t utilize roles. Service account roles include client roles from the
realm-management.Configuring access rights for admin
Task management service account
The task management service account is utilized to facilitate process initiation, enable the use of the task management plugin (requiring the
FLOWX_ROLE and role mapper), and access data from Keycloak.”- Add a new client by selecting Clients then click Create.

- Next, set the following properties:
- Access type - confidential
- Service Accounts Enabled - ON

- Go to Clients → realm-management → Roles and add the following service account client roles:
- view-users
- query-groups
- query-users

- Configure a realm roles mapper:

- Assign the necessary service account roles, including
FLOWX_ROLE.
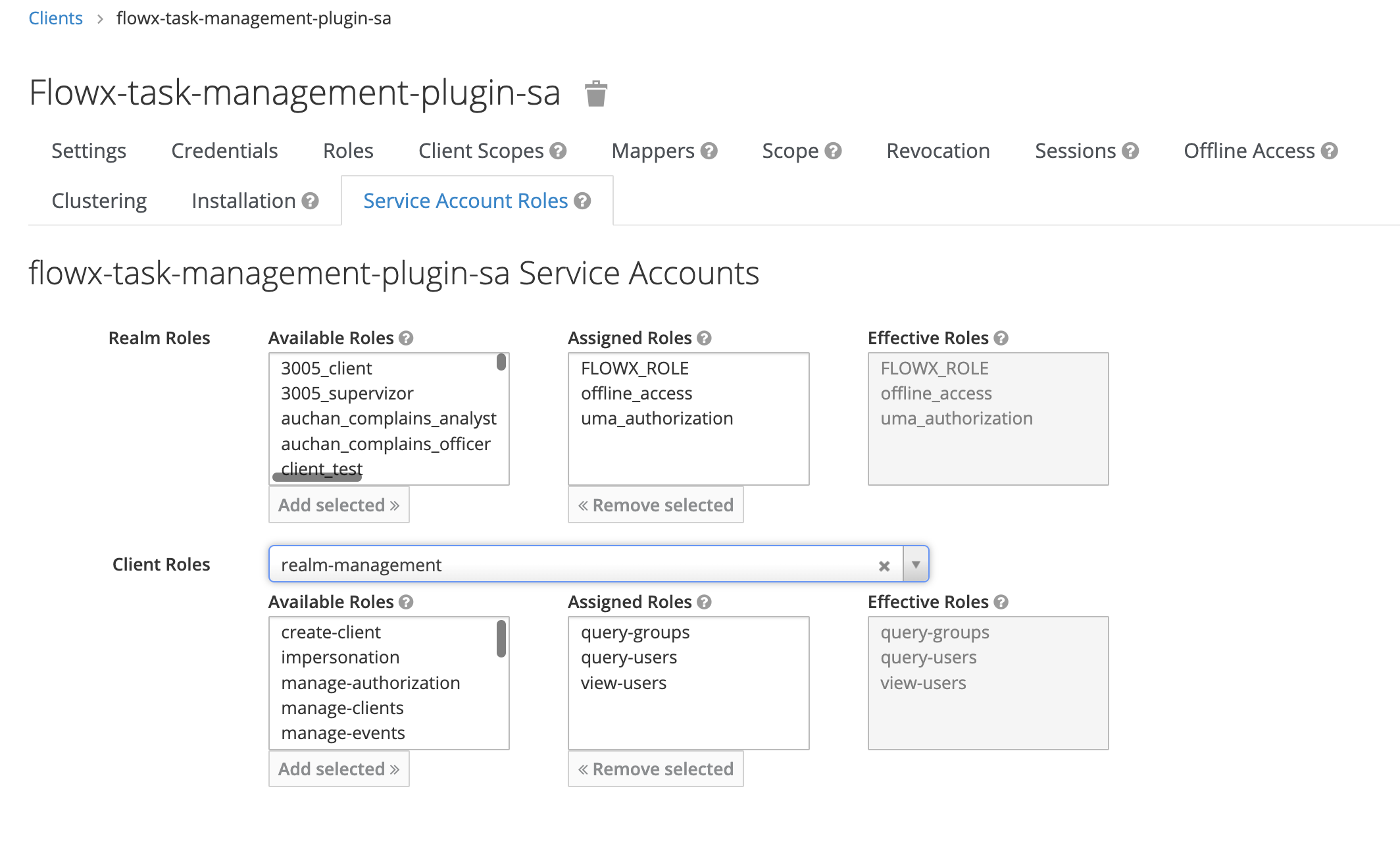 In the provided example, the task management service account can have the following assigned roles, depending on the required access scopes:
In the provided example, the task management service account can have the following assigned roles, depending on the required access scopes:
- view-users
- query-groups
- query-users
Configuring access rights for Task Management
Process engine service account
The process engine requires a process engine service account to make direct calls to the Keycloak API.This service account is needed so the use of Start Catch Event node is possible.
- Add a new client by selecting Clients then click Create.
- Next, set Access type as confidential and enable Service Accounts.

This service account does not require client roles.
- Assign the
FLOWX_ROLE(this is needed to run process instances).

- Add a realm-roles mapper:

Scheduler service account
This service account is used for Start Timer Event node. The registered timers in the scheduler require sending a process start message to Kafka. Authentication is also necessary for this operation.
- Add a new client by selecting Clients then click Create.
- Next, set Access type as confidential and enable Service Accounts.
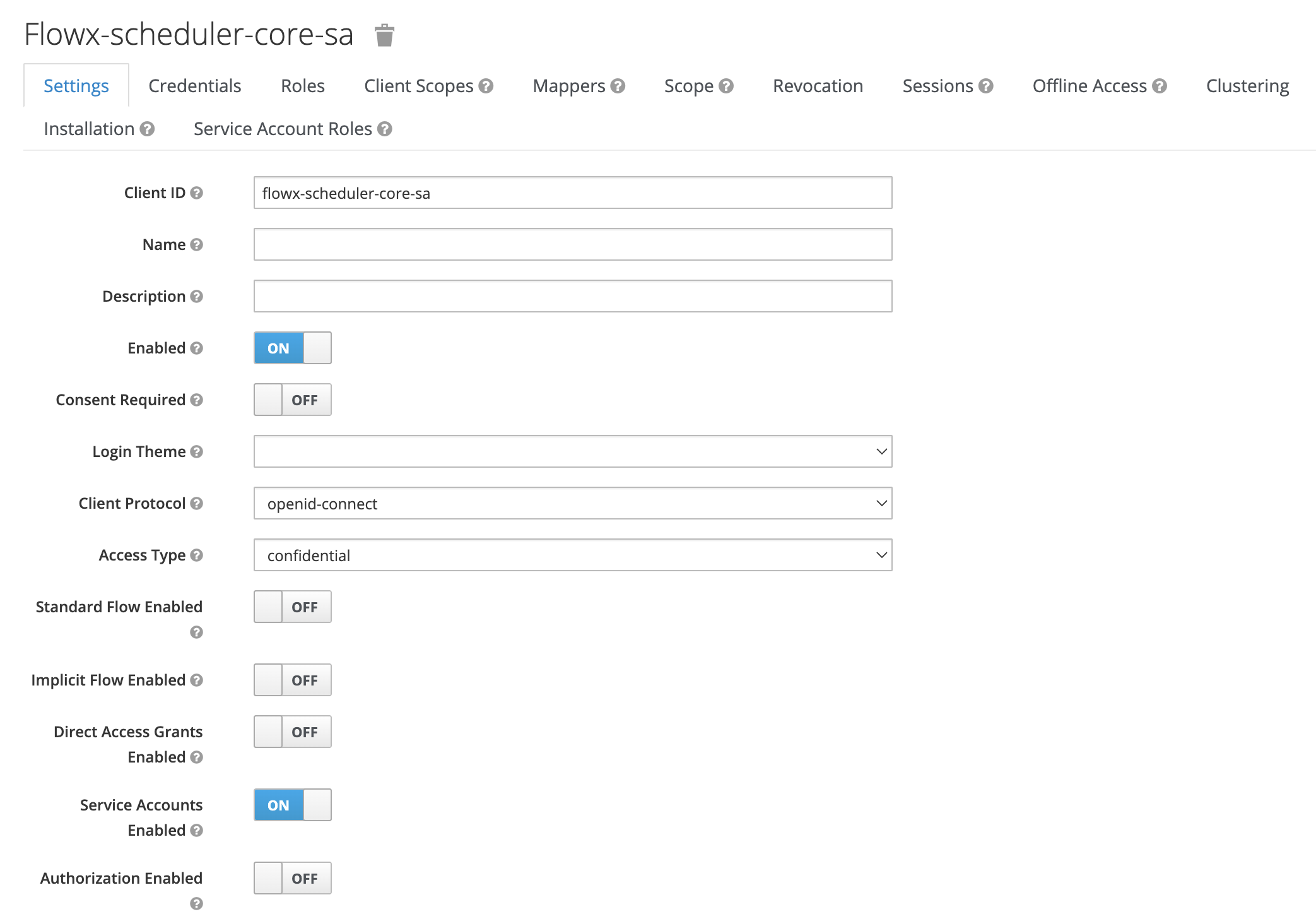
- Assign the
FLOWX_ROLEas service account role (this is needed to run process instances).
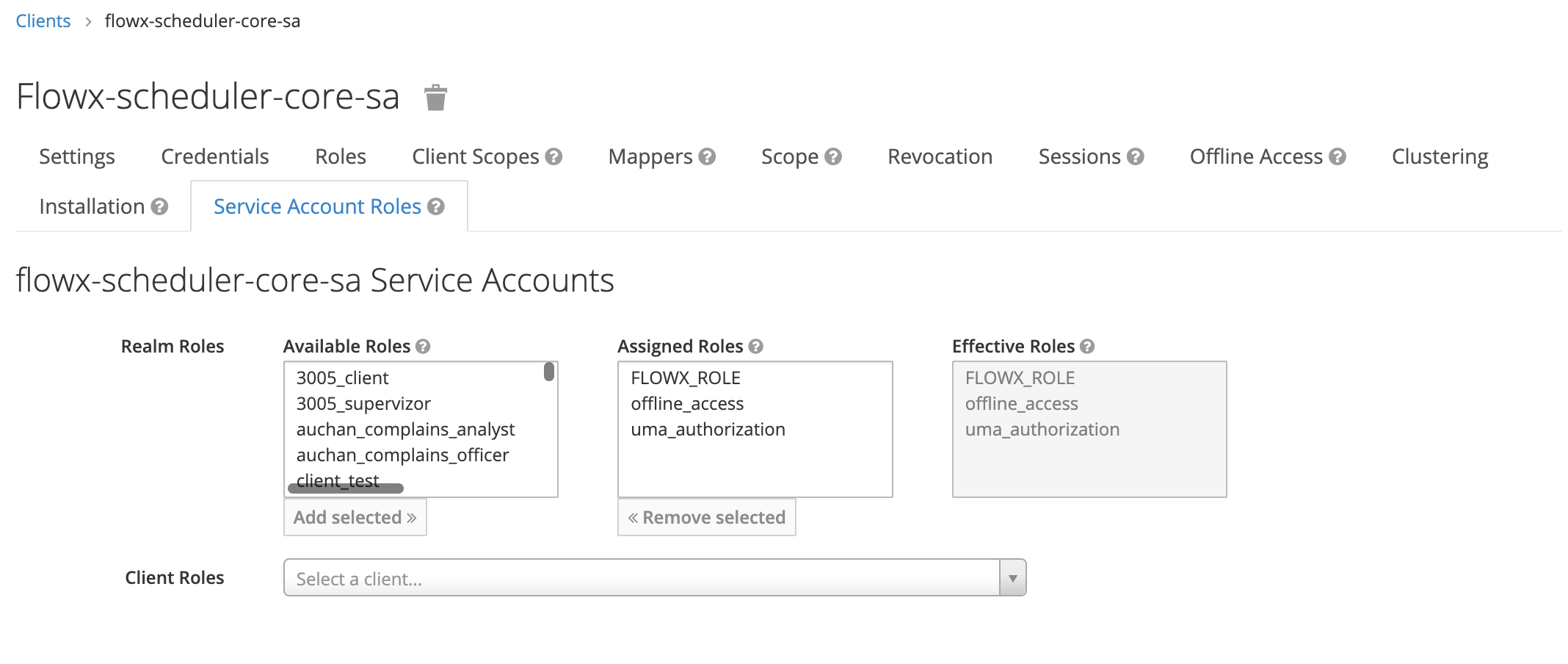
- Add a realm-roles mapper (as shown in the example for process-engine service account).

